Now it is available my session on VMUGIT 2023

Now it is available my session on VMUGIT 2023

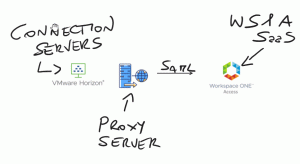
When we need to integrate a Horizon infrastructure to the cloud identity provider (like Workspace One Access SaaS solution) sometimes we need to manage firewall and proxy configuration.
For the Firewall rule, there is much information (KB link) while for the proxy server, we are not able to use Windows server configuration because Horizon ignores it.
To use a proxy server to permit communication to the IdP URL from Horizon Connection servers we need to configure some values on ADAM DB:
pae-SAMLProxyName
pae-SAMLProxyPort
To connect to ADAM DB and where modify the correct value
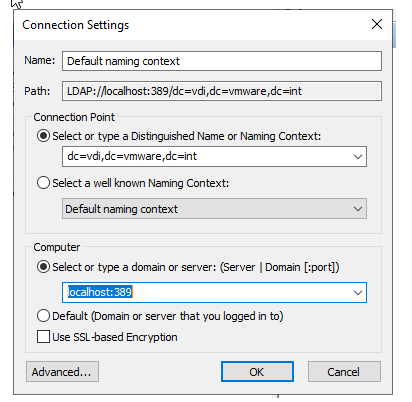
dc=vdi,dc=vmware,dc=int
localhost:389
pae-SAMLProxyName -> With Proxy URL
pae-SAMLProxyPort -> With Proxy Port
Now we can configure the SAML integration from Horizon and IdP
Some information about why we need to integrate and use Workspace One Access with Horizon:
Integration between VMware Horizon and VMware Workspace ONE Access (formerly called Workspace ONE) uses the SAML 2.0 standard to establish mutual trust, which is essential for single sign-on (SSO) functionality. When SSO is enabled, users who log in to VMware Workspace ONE Access or Workspace ONE with Active Directory credentials can launch remote desktops and applications without having to go through a second login procedure.
Broadcom ha acquisito VMware, ormai lo sappiamo tutti.
La situazione di incertezza aleggia ovunque soprattutto sul mondo vSphere e sui costi (con tanti competitor che provano a ritagliarsi la loro fetta di mercato togliendole al leader indiscusso di questi anni)
Finalmente in questi giorni incomincio ad avere i primi dati effettivi (Prezzi ecc…) su cui iniziare a fare i primi ragionamenti.
!!Attenzione non voglio dare giudizi ma voglio solo paragonare due offerte fatte allo stesso cliente che abbiamo dovuto rivedere a seguito del nuovo listino (E parliamo di prezzi di listino.. senza eventuali scontistiche)!!
Ragioniamo su un cluster vSphere con 3 nodi da 2 processori ciascuno da 16 core.
Con le precedenti licenze e il vecchio listino nello scenaro ipotizzato dovevamo considerare:
Con il nuovo listino e le nuove tipologie di licenze invece dobbiamo considerare:
Entrambe le soluzioni con 5 anni.
Da una prima analisi le prime valutazioni sono:
Con il nuovo listino si viene a pagare circa 30-35% in meno.
Ho una semplificazione nella quotazione (una sola voce rispetto alle 4 precedenti)
Ovviamente:
ma aspettavo di avere due informazioni reali per fare le mie prime considerazioni.
L’unica cosa che posso dire è di valutare con attenzione il cambio …. (io sono il primo che accetta nuove sfide..) ma attenzione a tutti i prezzi nascosti e valutate bene!
P.S. se qualcuno ha delle esperienze in merito … condividiamole.

As usual, every 3 months VMware releases a new version of Horizon (and also of almost all EUC applications)
The following have been available for a few days:
Horizon 8 2312
App Volumes 4 2312
Dynamic Environment Manager 2312
ThinApp 2312
Among the various features released for Horizon 8, the most interesting one is Agent Auto Upgrade:
“The agent auto upgrade feature allows customers to automatically initiate upgrades without manual intervention. To utilize this feature, on-premises systems must have access to CDS servers. Customers without CDS access can establish their webserver, host the agent components, and then register the agent build with the connection server to upgrade agents in VDI/RDSH desktops. This feature requires Horizon Plus or Horizon Universal License, and is available for Full Clone Desktops and RDSH Servers only. To upgrade Horizon Agent in Instant Clone Desktop Pools or RDS Farms, upgrade Horizon Agent on the Golden Image and schedule maintenance to push the new image.”
If we have a problem with the Identity directory on Workspace One Access like that:
Failed to save domains. Resolving domains with the directory server failed with reason: [fienile.lan – Kerberos authentication failed for domain.]
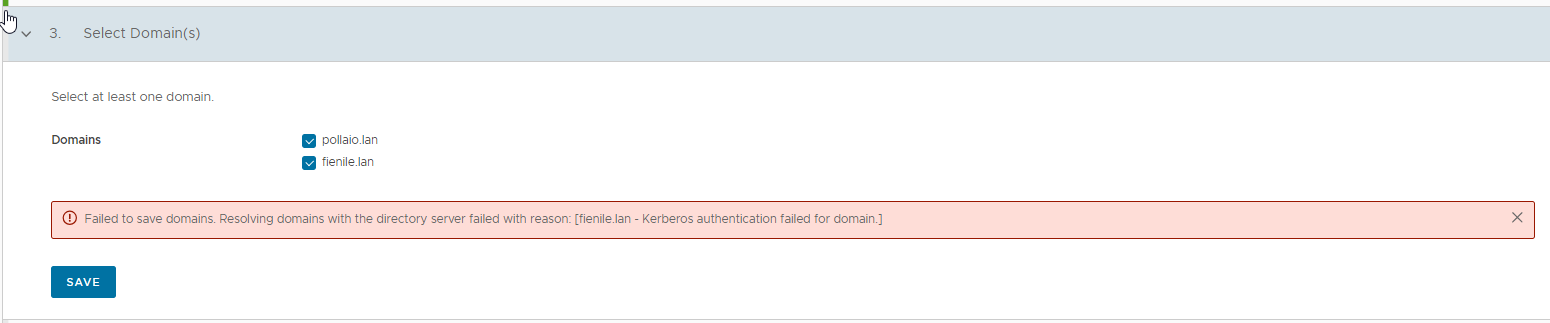
In the situation where we have an Active Directory with Multi-Forest Active Directory Environment with Trust Relationships (The trust needs to be two-way and direct (non-transitive)).
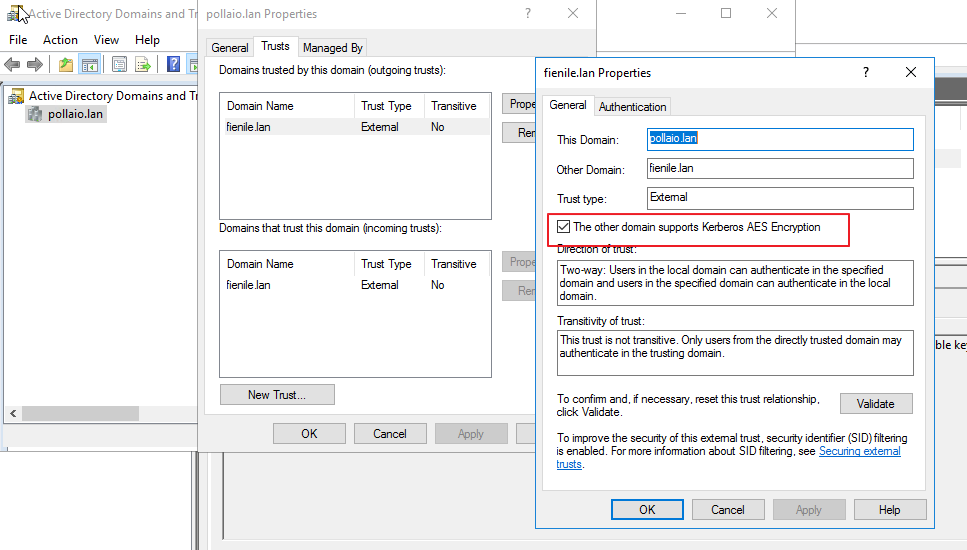
There may be a problem with the Trust configuration, and you can find this error on DC (the DC of the user configuration for the connection)
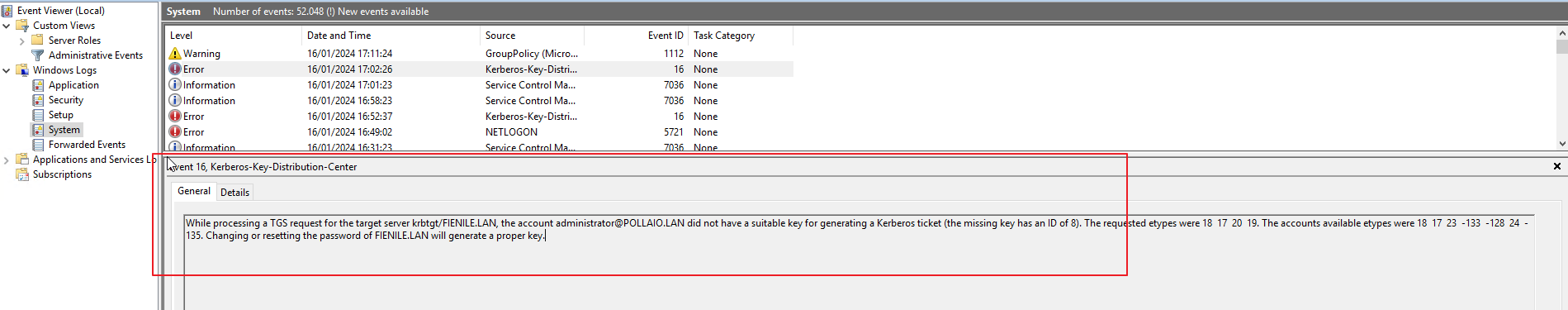
The solution is to change the trust configuration and add:
During the maintenance and updating of the Horizon Connection server components, one aspect is the necessary wait for the connection servers to correctly resume responding on TCP port 443.
During one of the many activities on Horizon my customer created a simple and effective door test script.
Even though it is very simple and intuitive, I want to share the code with you:
do {
$check = netstat -ano | findstr 0.0.0.0:443
"Waiting 5 seconds and retry"
sleep 5
} while (!$check)
$checkIn recent days, a customer reported an anomaly on an HPE SimpliVity cluster hosting instant clone Horizon VDIs. In detail:
After a careful analysis, we identified that there were no problems at the vSphere infrastructure level.
The issue was due to a Simplivity feature called IWO.
By disabling IWO and keeping DRS active (Full automatic) I have an optimal balance of CPU and RAM load between hosts at the expense of a slight increase in I/O trip times
I want even VM load across my cluster in terms of CPU and memory. Data locality and I/O performance are not top priorities. Most applications are CPU and memory intensive, and adding 1ms to 2ms to I/O trip times will not impact application performance.
In this scenario, IWO can be disabled thus ensuring no DRS affinity rules are populated into vCenter server. Suppressing DRS affinity rules will allow VMware DRS or allow you to directly distribute VMs across the cluster as desired to ensure all VMs are adequately resourced in terms of CPU and memory. The ‘Data Access Not Optimized’ alarm can be suppressed within vCenter server.
More information:
Many times I found myself having to demonstrate that the communication between the Unified Access Gateway and the Connection Servers was not working due to problems with poorly configured firewall rules. A very useful test is to connect to the UAG console and launch the classic CURL command:
curl -v -k https://<FQDN or IP ADDRESS CS>:443/
the outcome of which is as follows if the connection is ok (HTML output)
or the following if the connection is not enabled on the firewall
More info and tools here:
In this guide, we will analyze how to configure ControlUP COP (ControlUP on-Premise) to monitor a VMware Horizon 2309 infrastructure with Instant Clone Desktop Pools (we will not cover the installation part of the product)

The following steps are required:
Requirements for the server part:
COP Server |
COP Server | Console Machine |
| Machine | Windows Server | Windows Server orWindows |
| Operating System | Windows Server supported versions:2022,2019,2016 | Windows Server supported versions:2022,2019,2016 OR Windows 11, 10 |
| CPU* | 2 CPUs | 2 CPUs |
| Memory* | 8 GB RAM | 8 GB RAM |
| Disk Space* | 10 GB | 10 GB |
| Required Software & Permissions |
|
.NET Framework 4.5 or later |
Requirements for Part DB:
| MSSQL Versions (Standard, Enterprise, or Express) | Maximum Database Size | Collation |
| 2022,2019,2017,2016,2014 | 10 GB | SQL_Latin1_General_CP1_CI_AS |
Requirements for the VDI part:
ControlUp Agent |
ControlUp Agent |
| Machine | No server installation necessary. Deployed onto Windows machines that are monitored by ControlUp(Linux monitored via API). |
| Operating system | Windows Server supported versions: 202220192016 (Core or Full)ORWindows 11, 10 |
| Required installed software | .NET 4.5 or later |
| TCP PORT | 40705 |
A Service Account to access the Horizon infrastructure:
The Read-Only role is sufficient for all monitoring purposes. If you want to perform built-in Horizon actions, then the service account needs the following permissions:
So what is needed is:
Download the version of ControlUP COP from the VMware site
Log in to the customer portal and in the product area under Desktop & End-User Computing
Log in to OEM Addons
Download the on-premise version
Perform the basic installation
Once the COP version is installed and the console is installed, log in to our ControlUP installation
How to install the agent on the GoldImage:
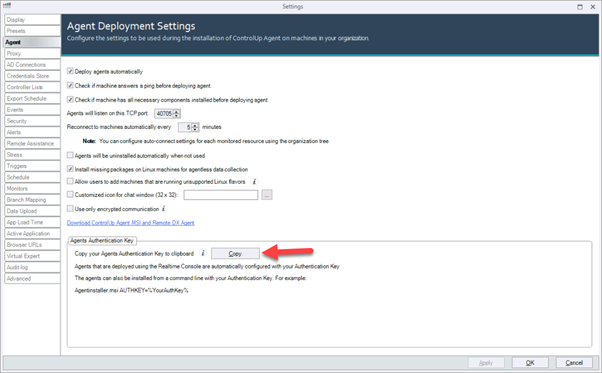
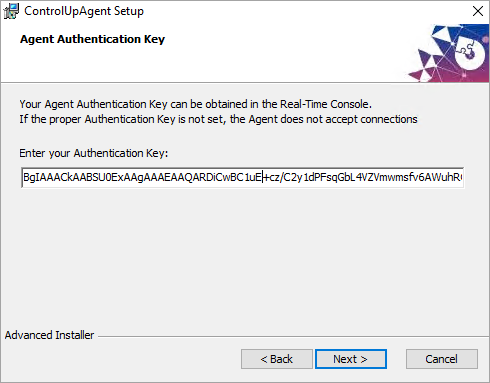
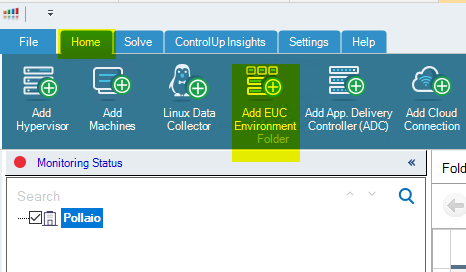
Now from the ControlUp Management console, we are able to:
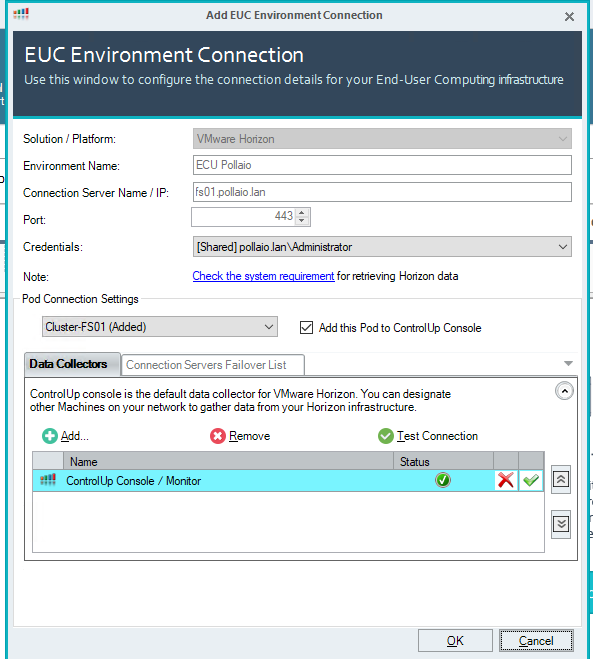
Add Horizon infrastructure:
Add the infrastructure info
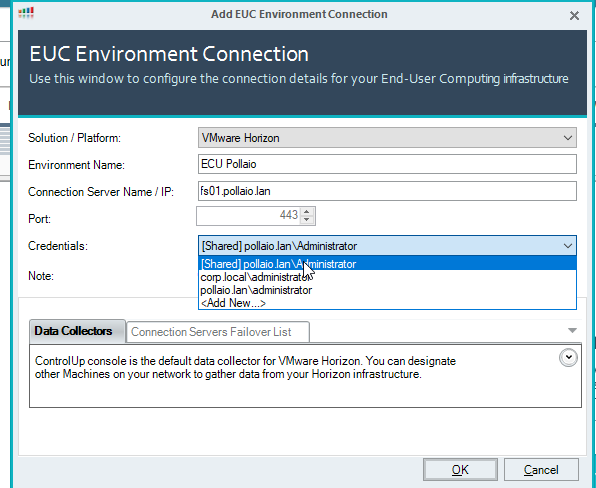
Click on OK
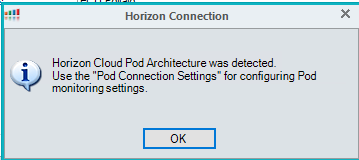
Add the pod to the console
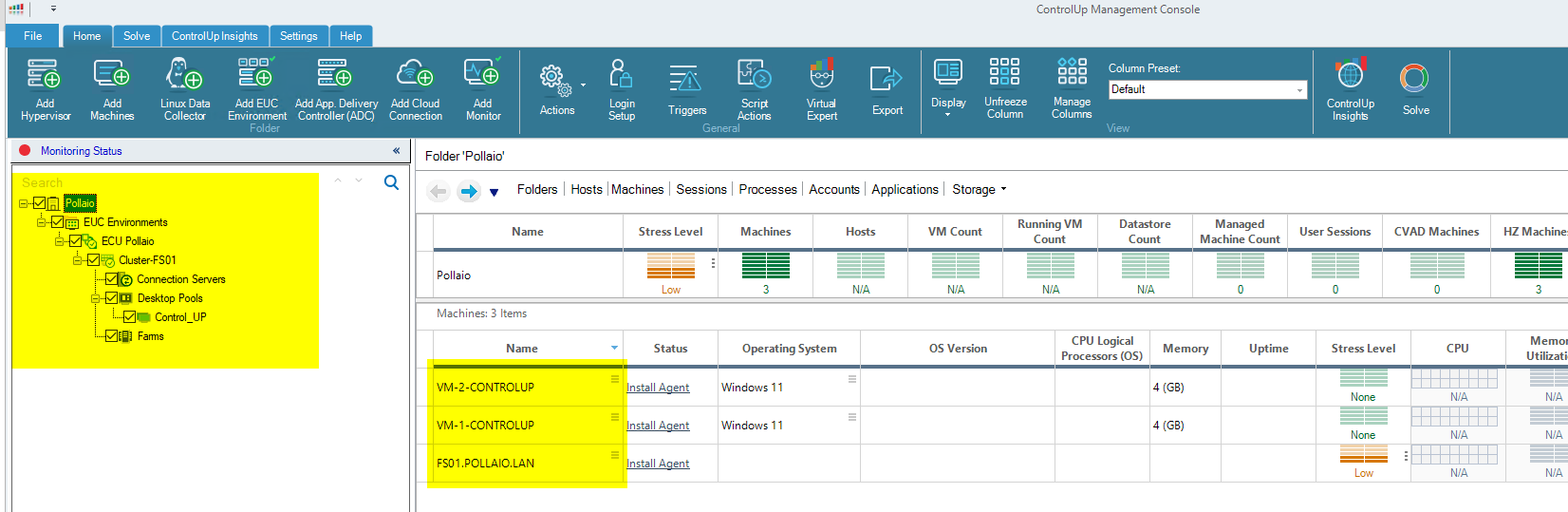
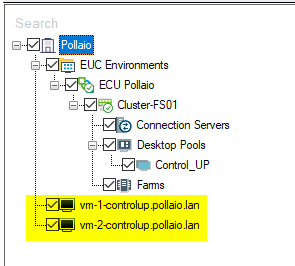
Now on the left panel, we have our Horizon infrastructure added.
To monitor correctly our instant clone (after adding the agent) we need to discover the VM like a Machine
Search with the partial name of the VDI machines
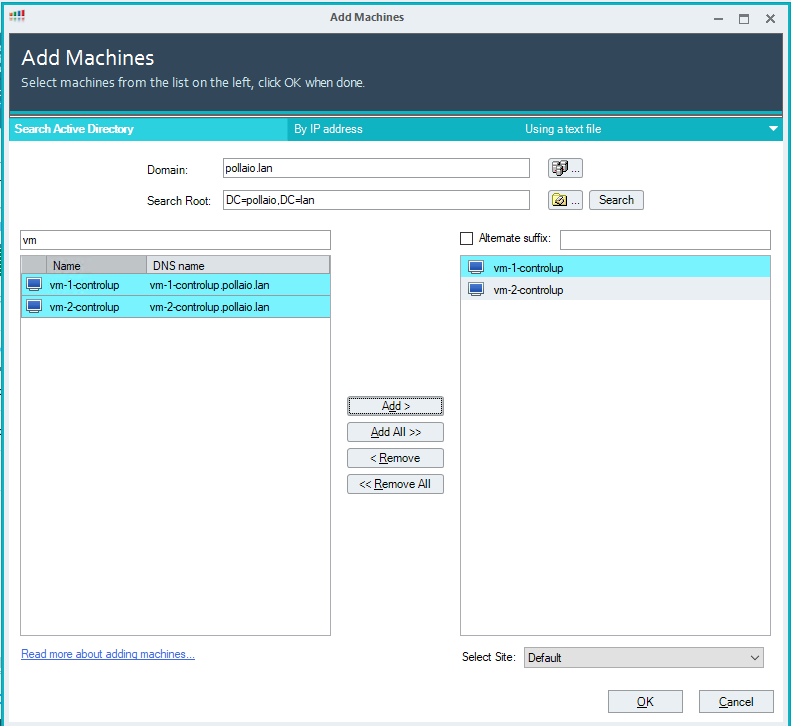
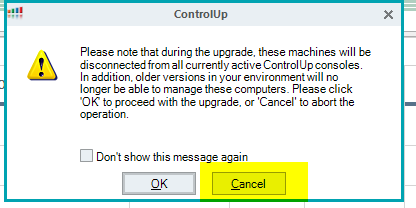
Select cancel
We are VM on the left control panel in black status
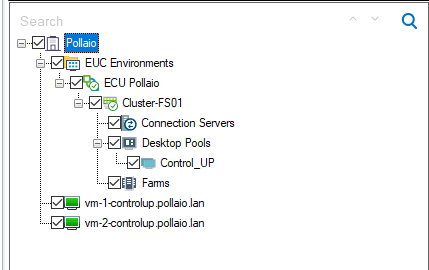
After a few seconds the VDI VM Goes to Green
Auto connect state must be enabled (this function is important when the instant clone VDI is removed and recreated).
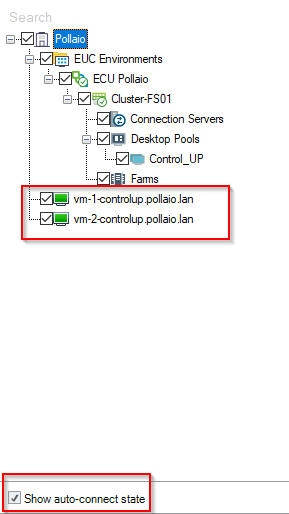
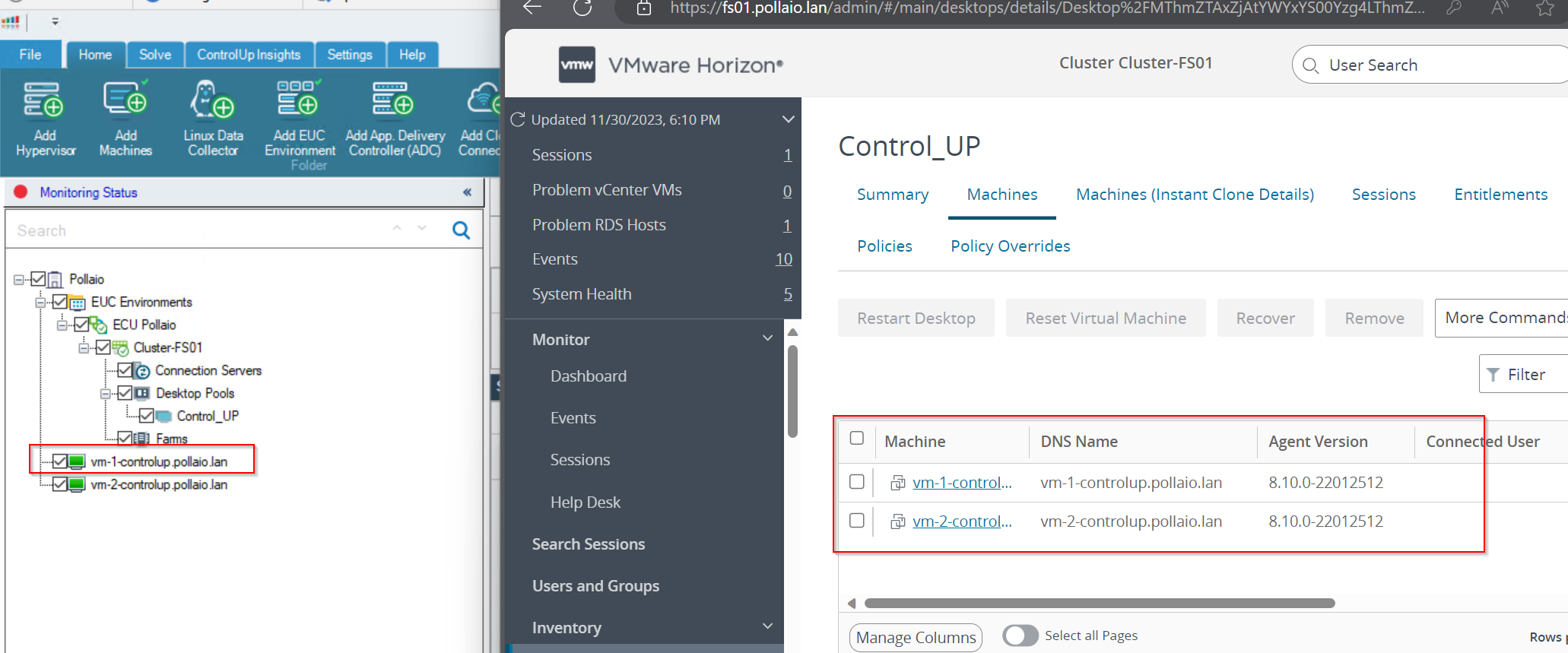
Now we can monitoring the Instant-Clone VDI
Check the VDI logon duration
Now we can manage and control the infrastructure, for example, to check the logon duration
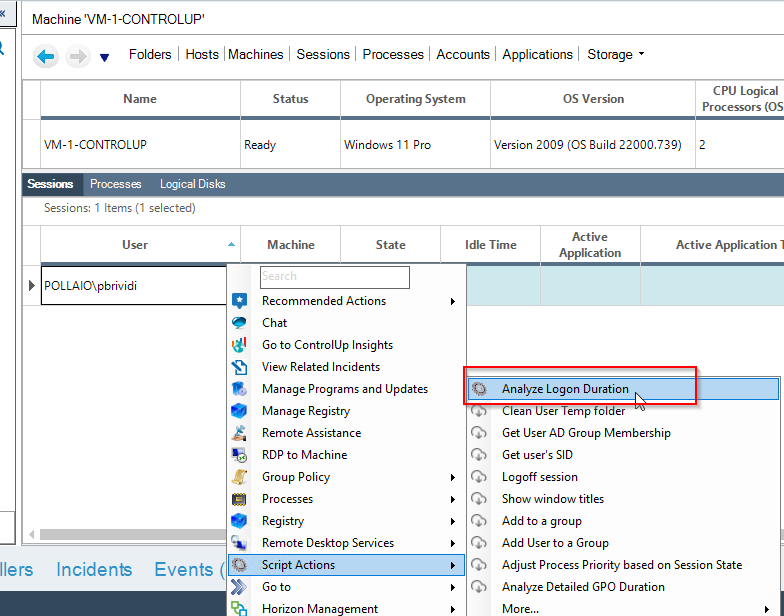
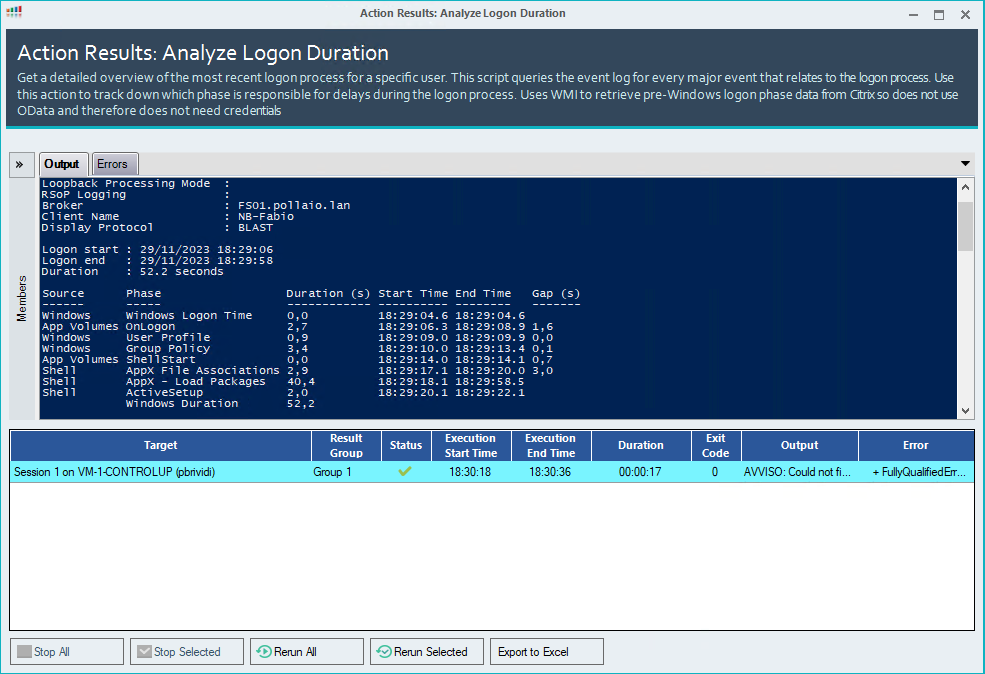
What happens when VDI instant clones are regenerated?
If a user disconnects from his VDI of the instant clone type, it is destroyed and recreated, on the ControlUp side this is put in the Red -> Yellow state until it returns to Green
When recreating
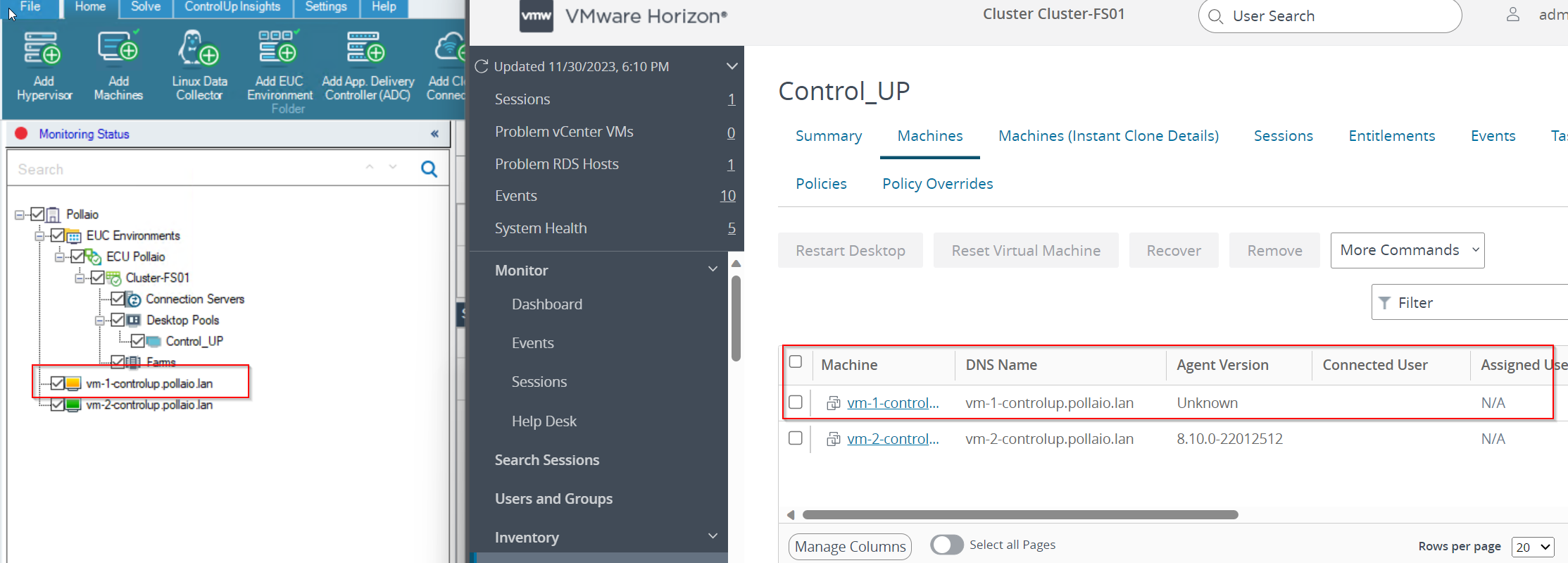
After recess
Dynamic inventory
For a dynamic inventory of VDI, we can use Synchronization with Universal Sync Script (I’ll talk about this in a future post)
EUC Synchronization with Universal Sync Script (controlup.com)
After installation, we can schedule or start manually the script to sync my ControlUP with my EUC infrastructure.
References:
How to Deploy the Agent on Your Master Image for PVS/MCS/Linked/Instant Clones (controlup.com)
EUC Synchronization with Universal Sync Script (controlup.com)
The release of new versions of VMware Horizon 8 each quarter of the year (to provide new features and resolve any security holes) entails the need to have a consolidated, conservative update procedure with the least impact on users.
Below I report the procedure that I am using successfully.
User impact:
Steps
After the horizon upgrade, test the Desktop Pool:
For upgrading three Connection servers all steps necessity of two hours
During the activities, the users connected to the VDI do not encounter any problems
The next step, after complete the Connection Servers upgrade, is to update the Horizon agent on the master image and delete the Connection Servers snapshot