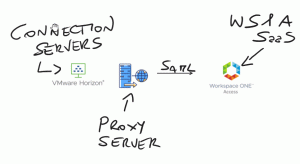
Publishing VDI outside our company network is an activity that has become a necessity for many companies since COVID-19 (employee smart working, workstations dedicated to consultants, etc.). In all the implementations, that I have done in recent years, one of the key points of my installations is the need to implement MFA solutions to increase the level of security.
In this post, I want to explain how to configure the integration of Workspace One Access WS1A, Horizon, and FIDO2 devices (I use a Yubikey 5 Series with NFC and Fingerprint)




What is VMware WorkSpace One Access?
Workspace ONE Access (vmware.com)
What is VMware Horizon?
VMware Horizon | VDI Software Solutions | VMware
What is FIDO2?
FIDO2 enables users to leverage common devices to easily authenticate to online services in both mobile and desktop environments.
The FIDO2 specifications are the World Wide Web Consortium’s (W3C) Web Authentication (WebAuthn) specification and FIDO Alliance’s corresponding Client-to-Authenticator Protocol (CTAP).
What is Yubikey 5 Series?
Multi-protocol security key, eliminate account takeovers with strong two-factor, multi-factor, and passwordless authentication, and seamless touch-to-sign. Multi-protocol support allows for strong security for legacy and modern environments. A full range of form factors allows users to secure online accounts on all of the devices that they love, across desktops and mobile.
- Multi-protocol support; FIDO2, U2F, Smart card, OTP, OpenPGP 3
- USB-A, USB-C, NFC, Lightning
- IP68 rated, crush resistant, no batteries required, no moving parts
USB-A YubiKey 5 NFC Two Factor Security Key | Yubico
Configure Workspace one Access(WS1A) SaaS for use FIDO2 authentication
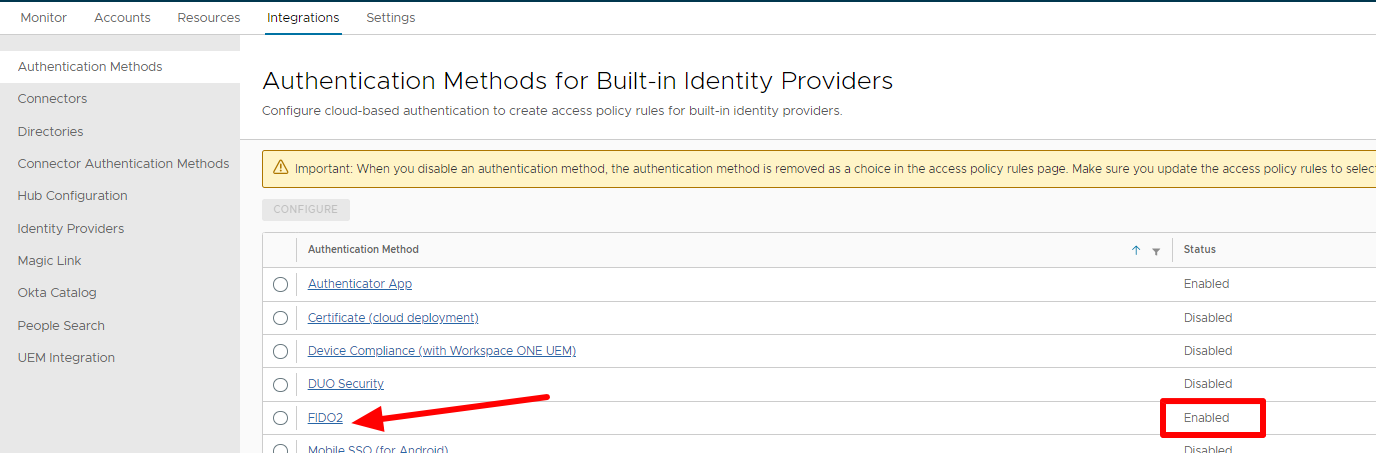
Enable Authentication methods on WS1A.
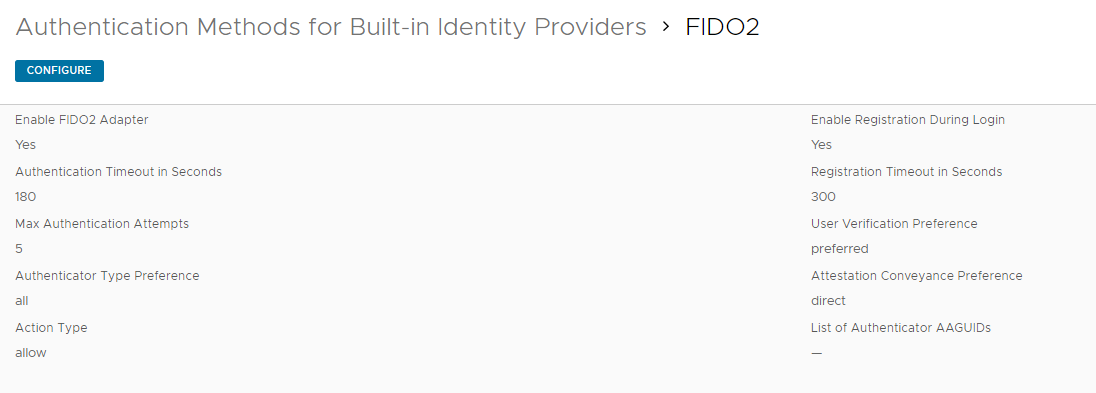
Go to integrations -> Authentication Methods -> Click on FIDO2 -> Enable FIDO2 Adapter
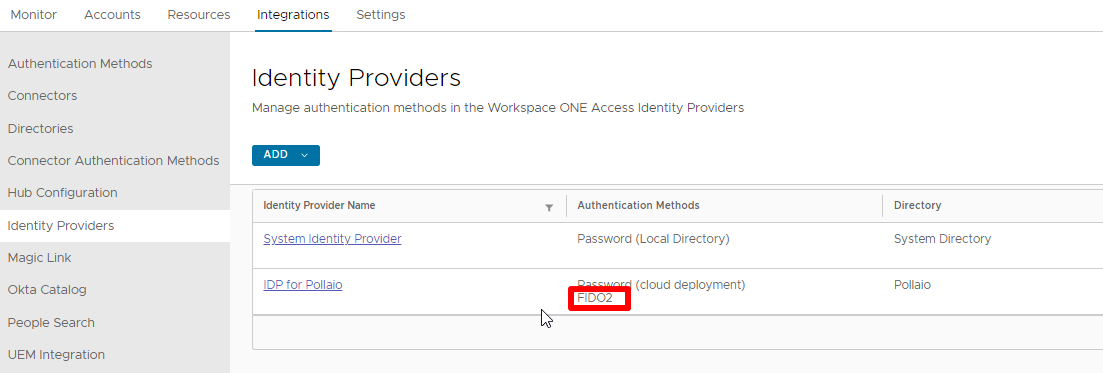
Now we need to associate the authentication method to Identity provider (created to integrate WS1A with Active Directory)
Go to integrations -> Identity providers -> Click on correct IdP -> Flag FIDO2
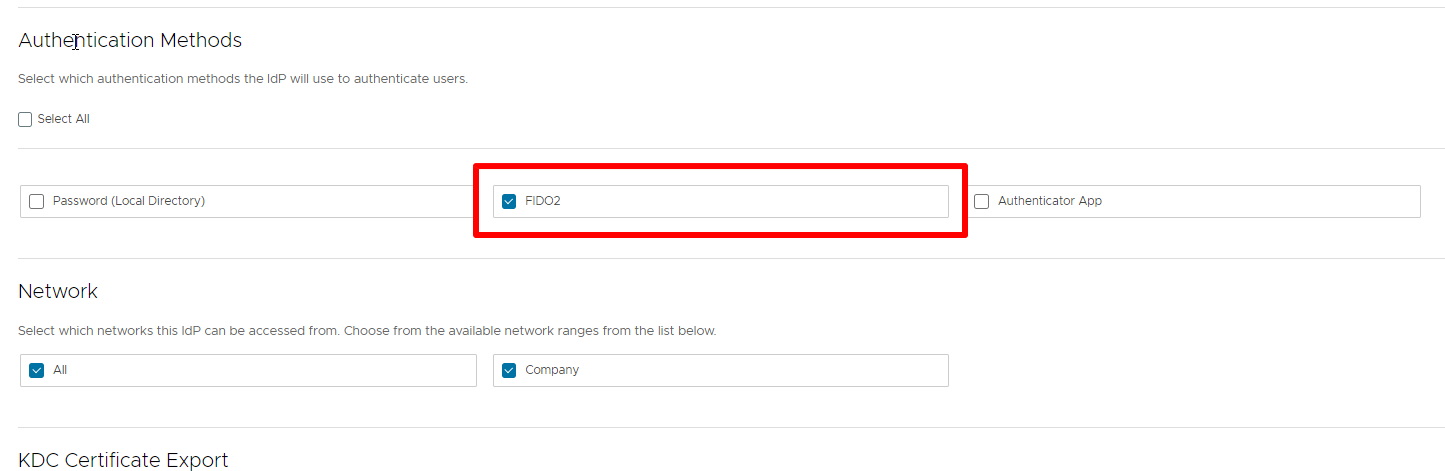
After associating the FIDO2 to IdP we need to create the policy to enable self-services FIDO2 device registration (it is possible to pre-configure the FIDO2 device registration)
Go to resources -> Policies -> Click on default_access_policy_set -> Edit
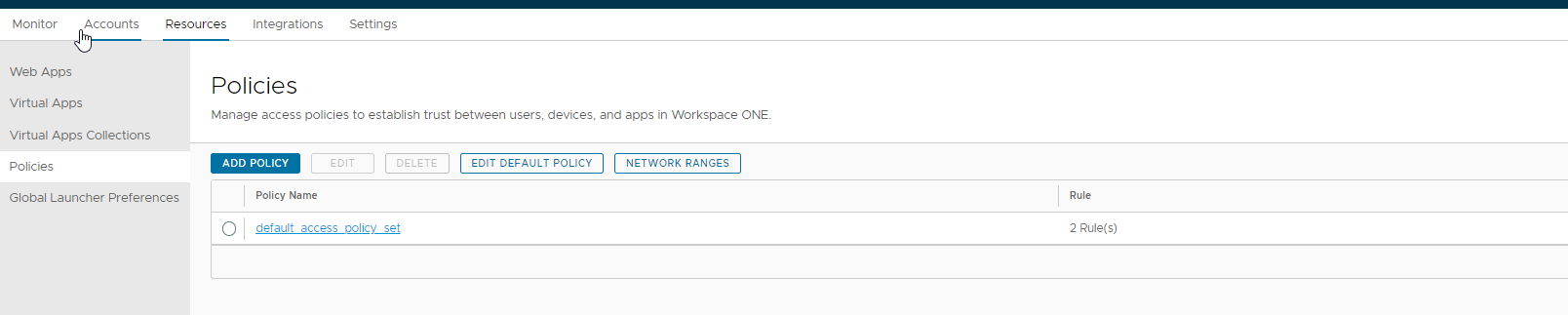
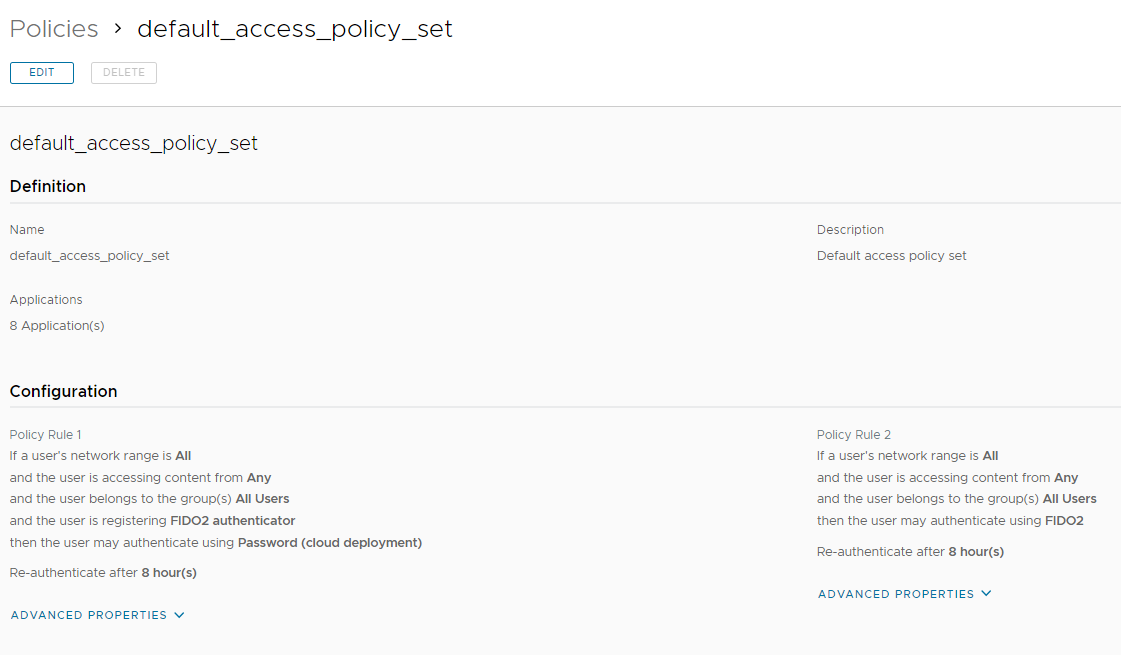
Create to rule:
Rule 1 -> enable self-service registration FIDO2 Device
Rule 2 -> enable the login with only FIDO2 Device
In the next image, there are the Policy Rule configurations
Self-service registration key
Insert the Yubikey 5 into to USB port and log to the Workspace One Access portal.
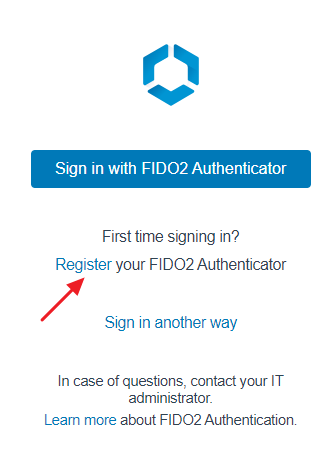
Now the web portal requires two choices:
- Sign in with Fido2 Authenticator
- Register your Fido2 Authenticator
To register the device we need to select Register
Login with the correct domain name account
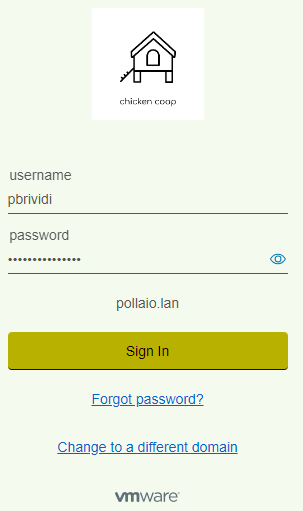
Now we need to select the authenticator
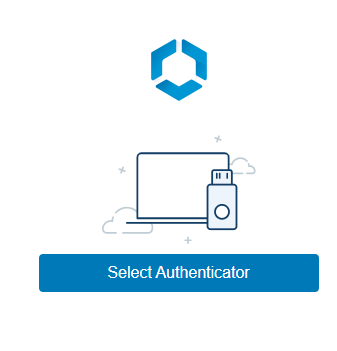
Select another device
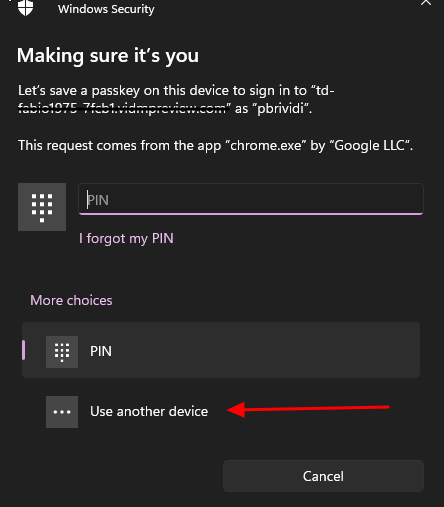
Select Security Key where store the passkey
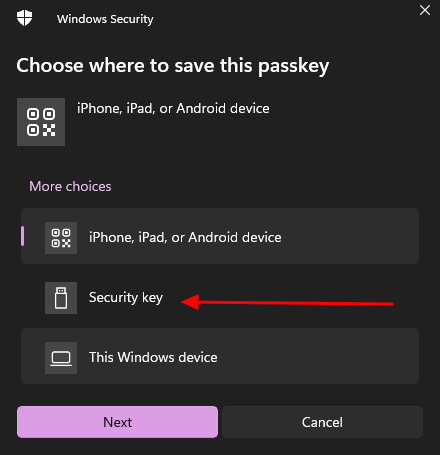
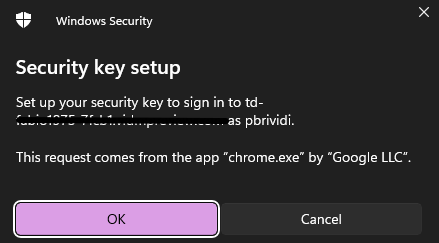
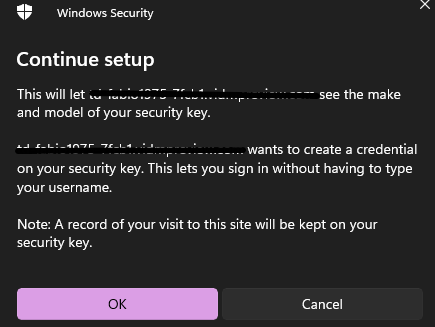
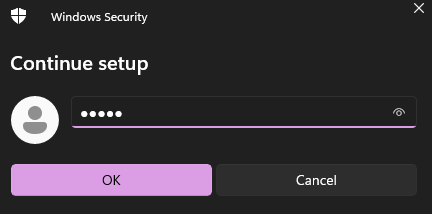
Insert the security pin
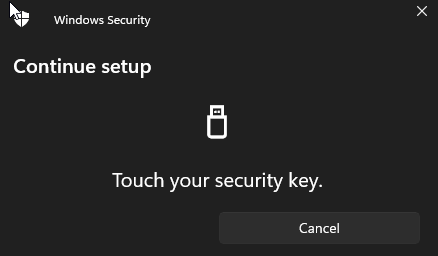
Touch the key (there is a fingerprint ….)
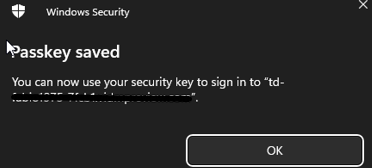
Add a name for the Security Key
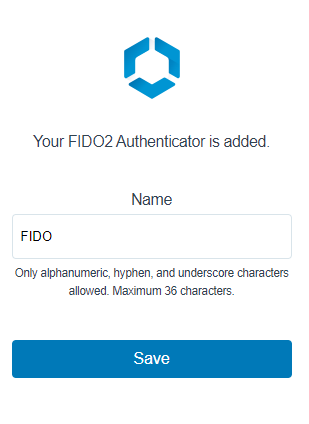
Now you are ready to log in with the security key
User Experience login
Access to company workspace one access website
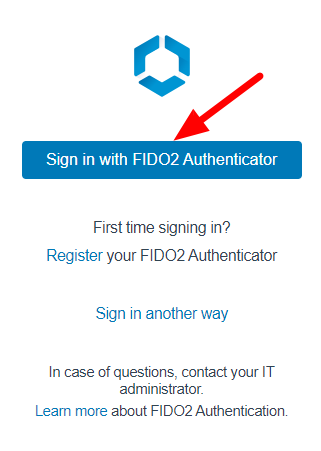
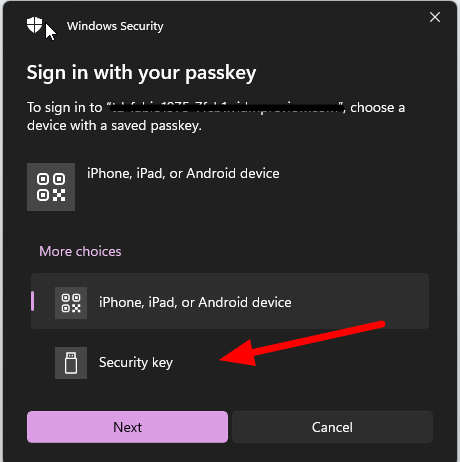
Insert PIN number associated with FIDO2
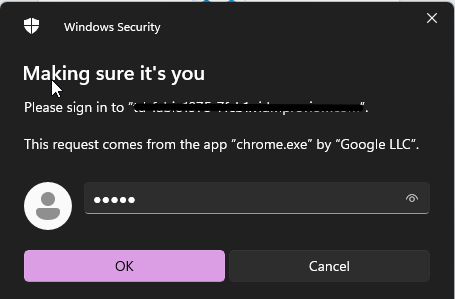
Now touch the key for fingerprint authentication Chiara2013!
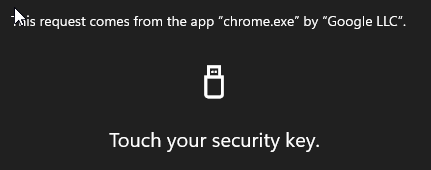
You are redirected to Workspace One catalog portal
If you want to show and reset the User FIDO2 device you need to:
Login to Workspace One Access SaaS admin console, go to Accounts, Users and click on the user that you want to reset the device association
Select two-factor authentication
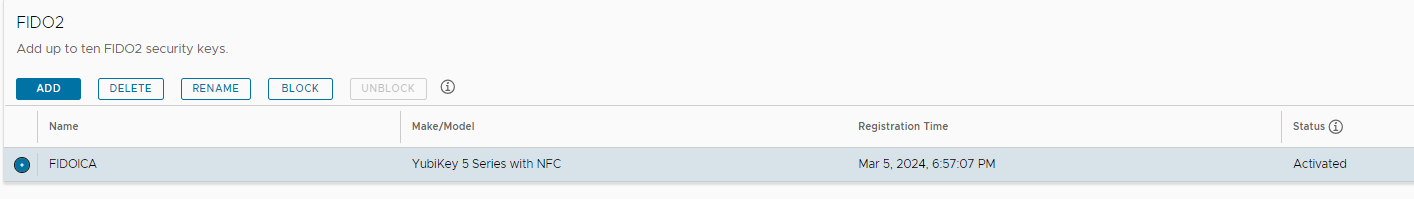
And delete the FIDO2 security key
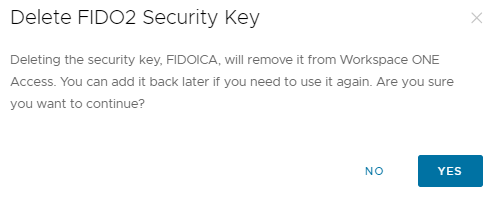
Otherwise, the administrator can associate the new device with the user.