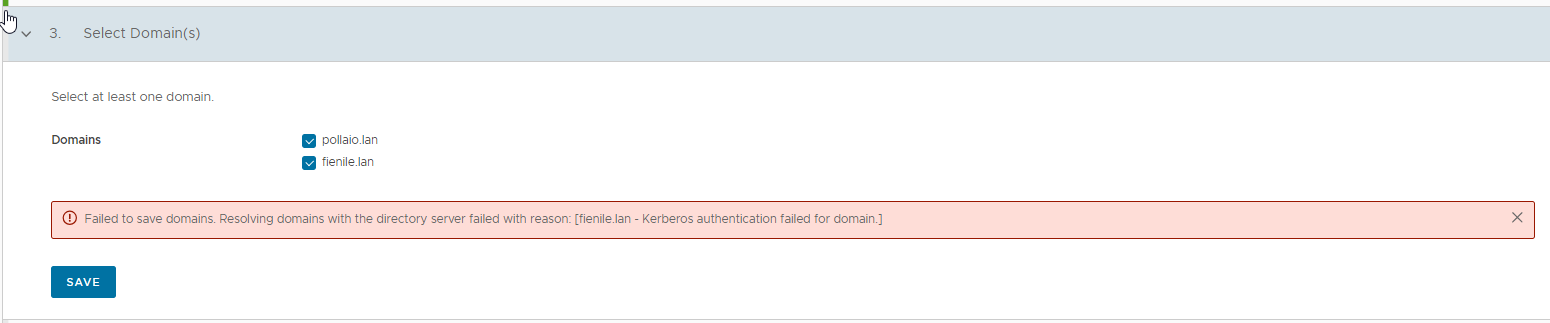
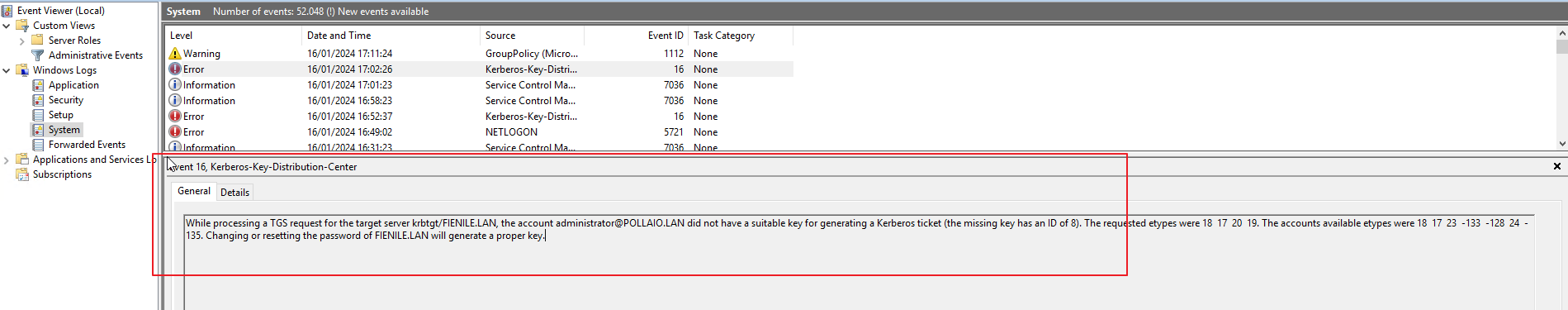
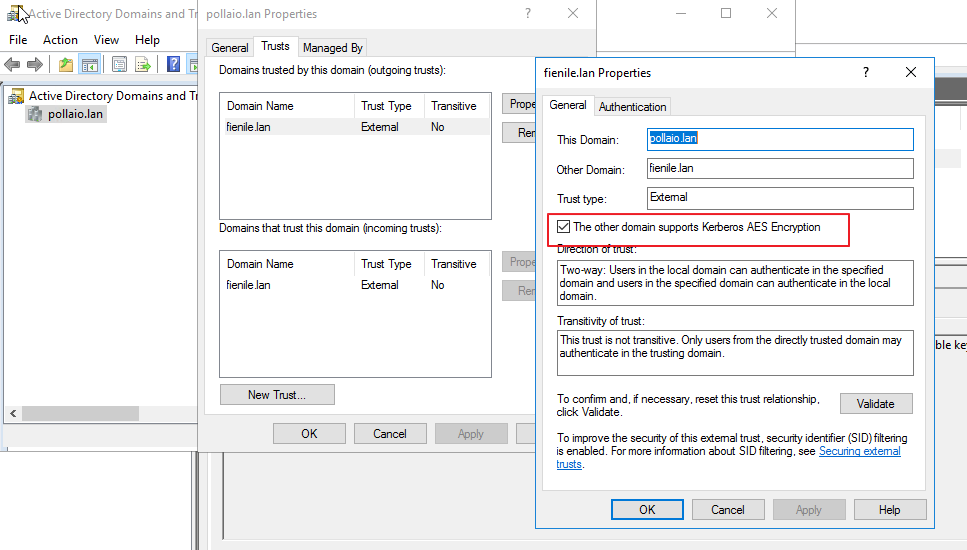
As usual, every 3 months VMware releases a new version of Horizon (and also of almost all EUC applications)
The following have been available for a few days:
Horizon 8 2312
App Volumes 4 2312
Dynamic Environment Manager 2312
ThinApp 2312
Among the various features released for Horizon 8, the most interesting one is Agent Auto Upgrade:
“The agent auto upgrade feature allows customers to automatically initiate upgrades without manual intervention. To utilize this feature, on-premises systems must have access to CDS servers. Customers without CDS access can establish their webserver, host the agent components, and then register the agent build with the connection server to upgrade agents in VDI/RDSH desktops. This feature requires Horizon Plus or Horizon Universal License, and is available for Full Clone Desktops and RDSH Servers only. To upgrade Horizon Agent in Instant Clone Desktop Pools or RDS Farms, upgrade Horizon Agent on the Golden Image and schedule maintenance to push the new image.”