When approaching the upgrade of an infrastructure in the EUC world (as with most technologies in the IT world) it is necessary to define a roadmap of activities and follow it carefully. In many cases, IT technology vendors already have update procedures in place that should be followed carefully. When I started working as a consultant, the documentation was very scarce (we are talking about the end of the 20th century and the beginning of the 21st…) and the procedures were poorly documented and only those who took courses or had experience could approach with a certain “tranquility” updates of production environments.
Going back to EUC infrastructures and focusing on the VMware by Broadcom world (still for a while….given the transfer of the technology in question) we have a precise update sequence, especially if we talk about + technologies that interact with each other, and the need to verify the interoperability between the various technologies.
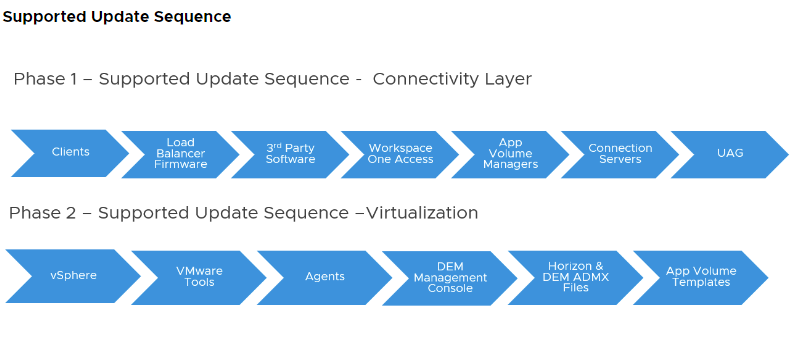
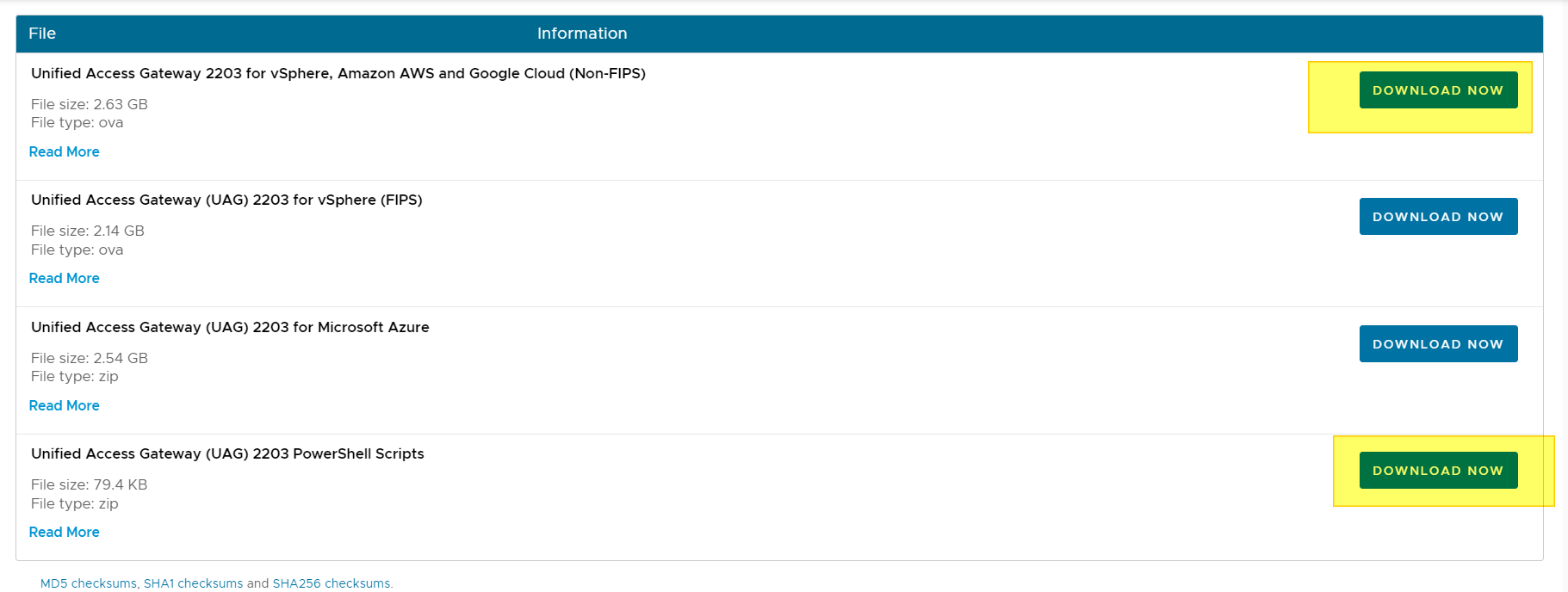
For example, we have this KB that gives us the upgrade sequence of a Horizon 8 infrastructure:
Update sequence for Horizon 7, Horizon 8, and compatible VMware products (78445)
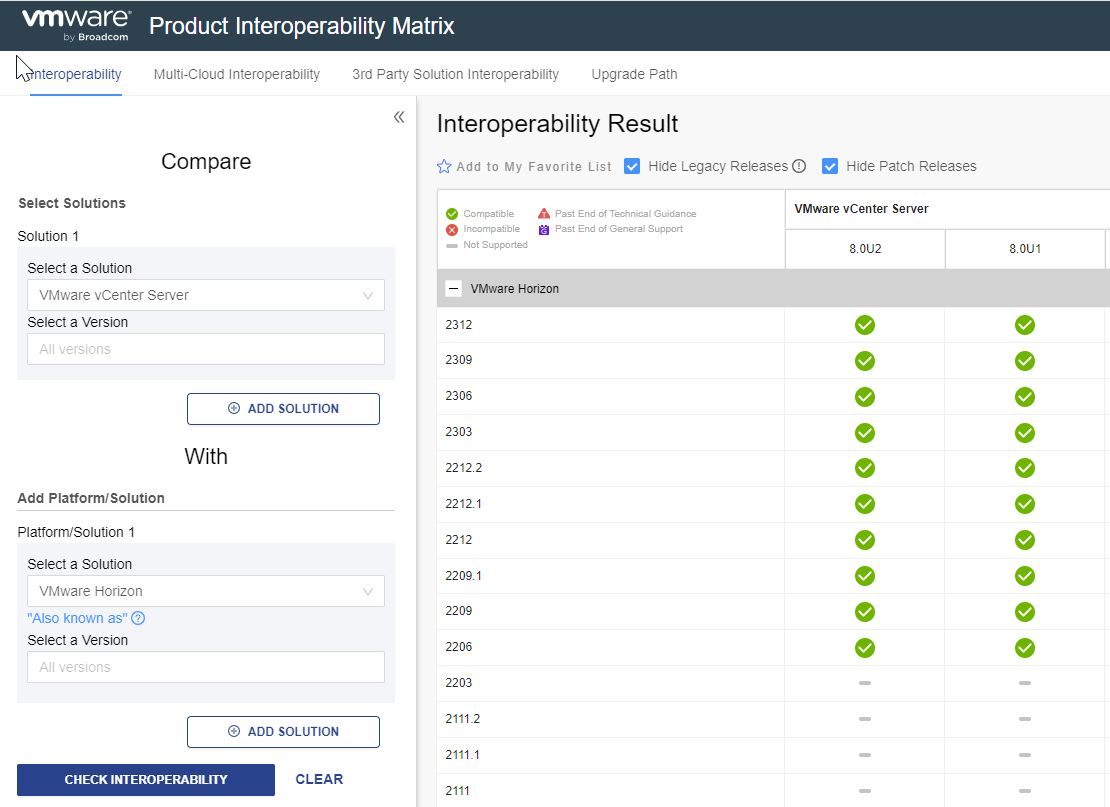
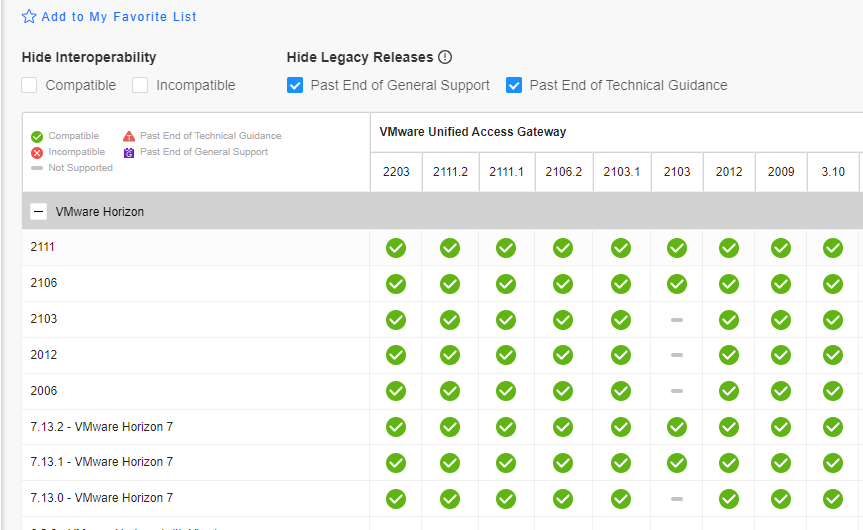
And the ability to use the interoperability portal:
https://interopmatrix.vmware.com/Interoperability
In my ten-year experience in updates and maintenance of vSphere and Horizon infrastructures, it has often happened that I have had to intervene and manage post-upgrade problems, where in most cases the problems were generated by the fact that I did not perform the update in the correct order or even did not complete all the upgrade steps.
For example, I have experienced situations where, following upgrades, the copy and glue to and from VDI sessions no longer worked correctly in a Horizon infrastructure.
In the end, the problem was solved by also performing the update step of the Horizon ADMX templates in Active Directory, something that the customer or whoever had done the update for him had not done.
![Notepad
File Edit Format
[General]
netlnternet=
View
Help
ipø=192.168.247.54
diskMode=
ip1=192,168,246.54
defaultGateway=192.168.247.1
target=
ds=
routes
2.168.246.1,192.168.4.0/24 192.168.246.1,172.25.2.0/23 192.168.246.1,172.25.6
netmaskØ=255.255.255. or
netManagement etwor
net3ackendNetwork
• pØA110cationMode=STATICV4
name=
deploymentOption=twonic
forceNetmaskØ=255.255.255. or
forceNetmask1=255.255.255. or](https://vmvirtual.blog/wp-content/uploads/2022/05/notepad-file-edit-format-general-netlnternet.png)
![Notepad
File Edit Format View Help
l[Generate1]
net Internet—DPG - EXT•4Zjjj)
ipe=192.168.247.55
diskMode—thick
source—E : - unified - access - gateway- 22.03. 1955Ø 91_OVFI Ø. Ova
ip1=192,168,246.55
default-Gateway=192.168.247.1
target—vi : / /vcaØ7
ds=vsanDatastore
routes1=172.16.e.Ø/16 192.168.246.1,192.168.4.0/24 192.168.246.1,172.25.2.0/23 192.168.246.1,172
netmaskØ=255.255.255. and
netManagementUetwork
net8ackendNetwork=DPG - INT - C*IZ
ipeA110cationMode=STATICV4
name-VilJAGØ3-22Ø3
deploymentOption=twonic
forceNetmaskØ=255.255.255. and
forceNetmask1-255.255.255. and
ip1A110cationMode=STATICV4
net-maski=255,255,255. and
authenticationT imeout—3ØØØØe
fipsEnab1ed—fa1se
sys L ogType=UDP
uagName=viuage3
clockSkewT01erance=6Øe](https://vmvirtual.blog/wp-content/uploads/2022/05/notepad-file-edit-format-view-help-lgenerate1.png)