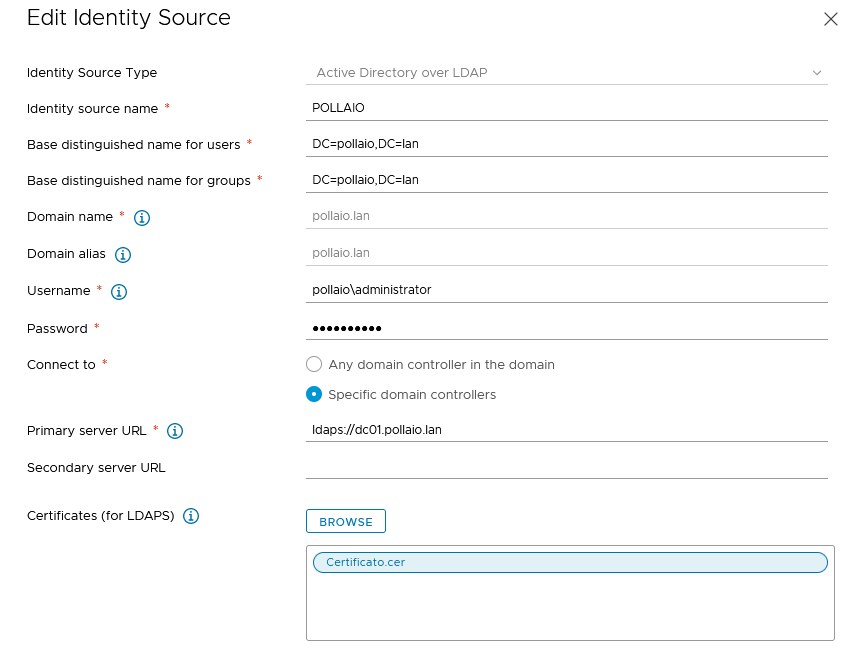
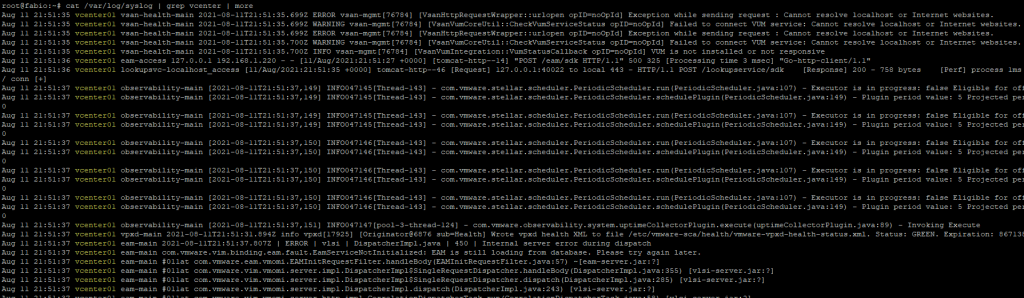
If we are removing a desktop pool from a Horizon infrastructure and we find ourselves in a situation that remains in a deleting state:
We can force the removal as follows:
- Remove any VDI VMs still in your vSphere infrastructure.
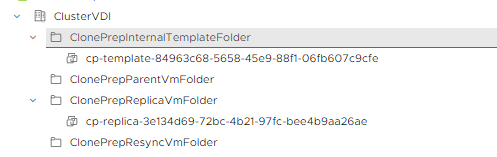
- Remove VM template, replication and parent.
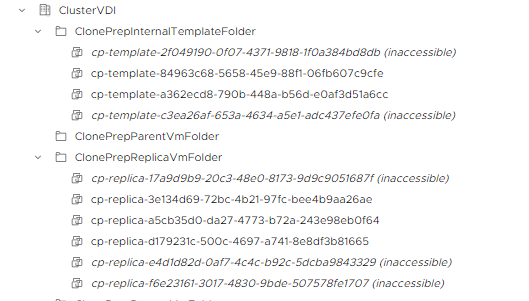
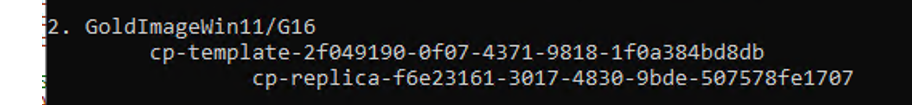
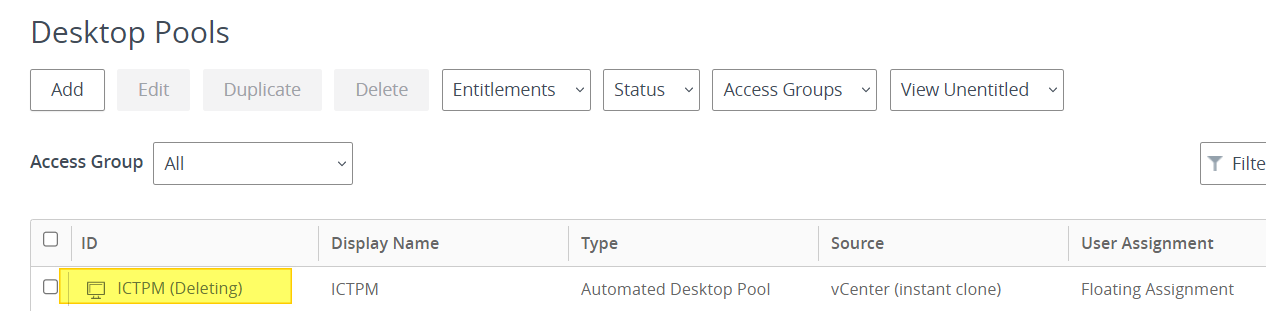
In my example, we have the following situation
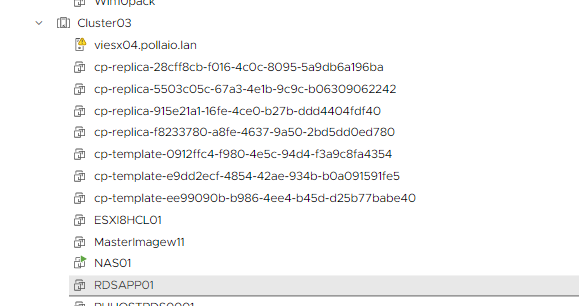
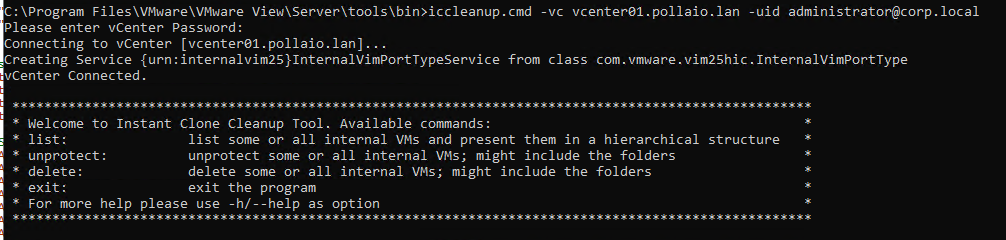
To remove them we use the tool iccleanup.cmd, we find te command on the connection servers by launching the following command to access:
iccleanup.cmd -vc <ome of vcenter> -uid < admin user of vcenter>
![]()
We enter the account password
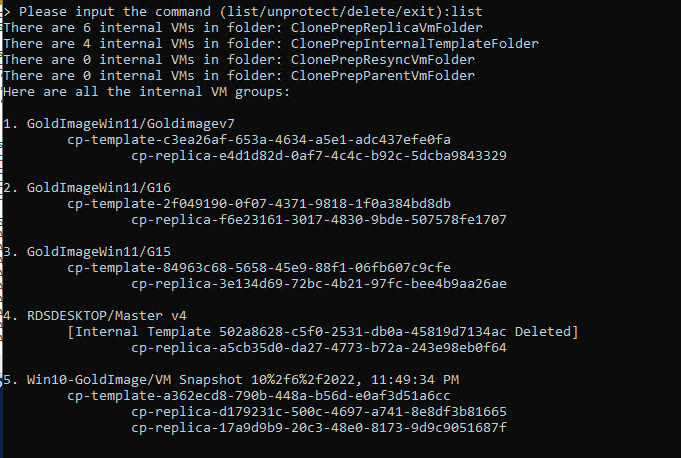
Run with the list command the list of service VMs to be deleted
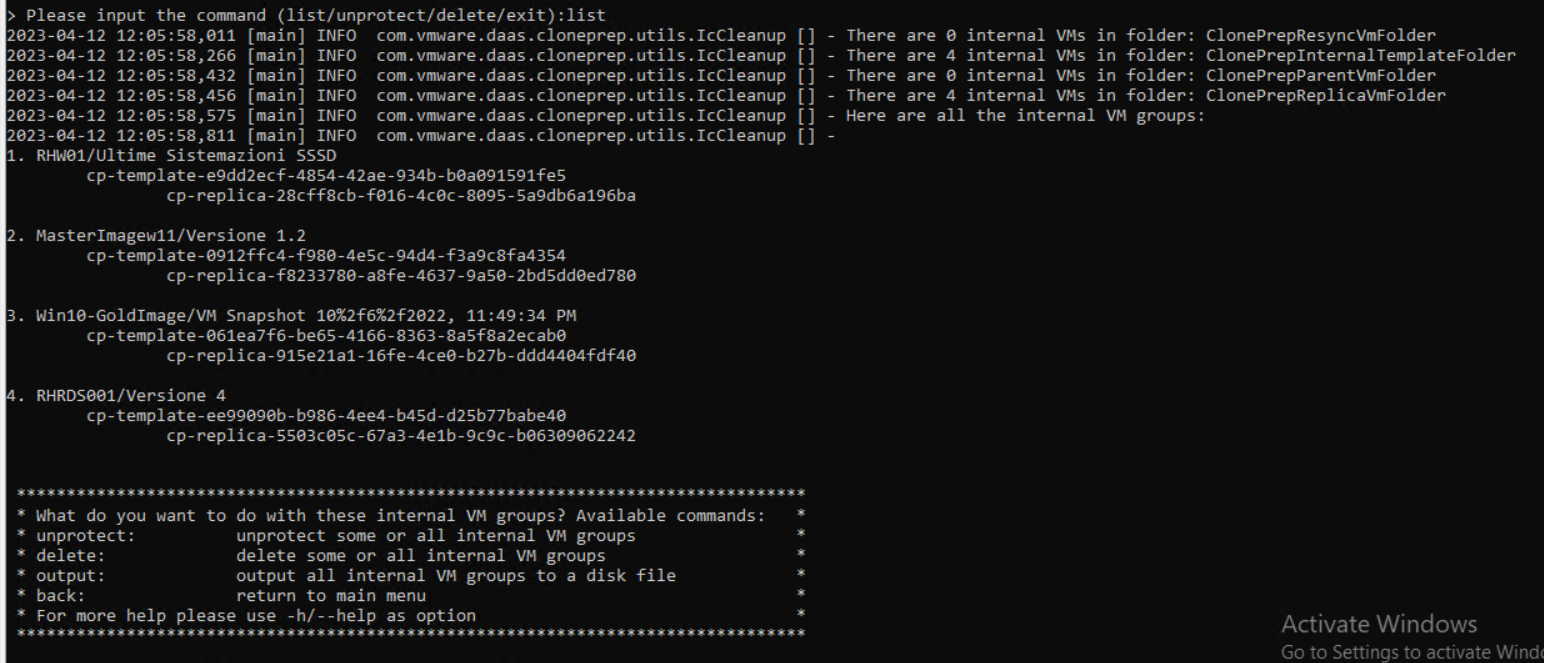
In my case, they are the VMs indicated with ID 2 and 3
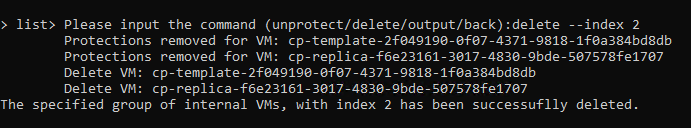
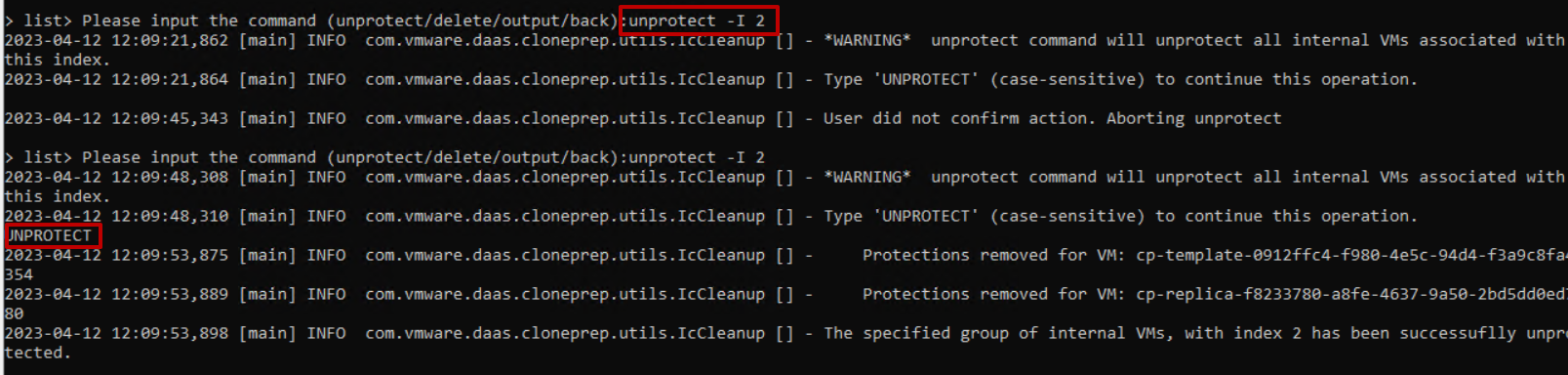
We start from 2 and first launch the unprotect indicating with -I the number 2 (unprotect -I 2) and confirm by writing unprotect
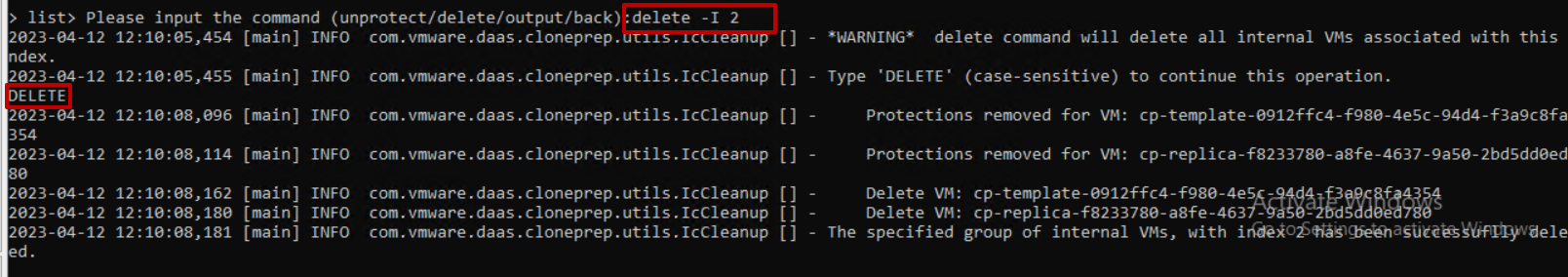
Then we delete with the question delete -I 2 and confirm by writing delete
Let’s go back by writing Back
Relaunch the List command and verify that Index has taken the other chain of system VMs to be deleted
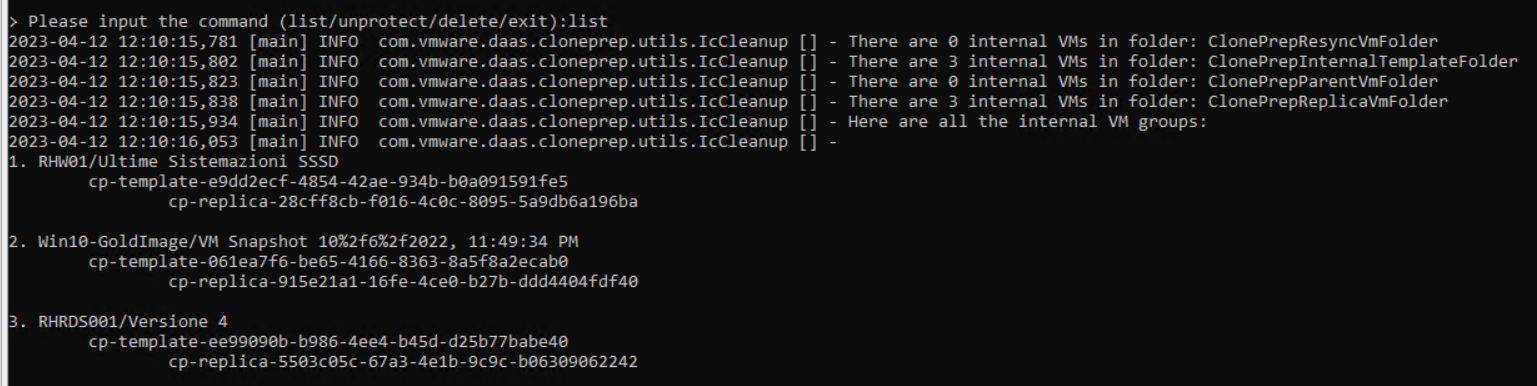
Ha was taken as index 2
We review the operations of unprotect and delete once again for index 2
At the end of the vCenter (they are service VM from other pools that should not be deleted)
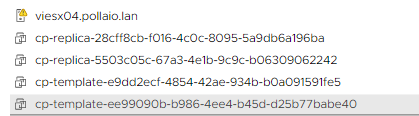
Already in this case, we may have deleted the DesktopPool that was in a deleting state.
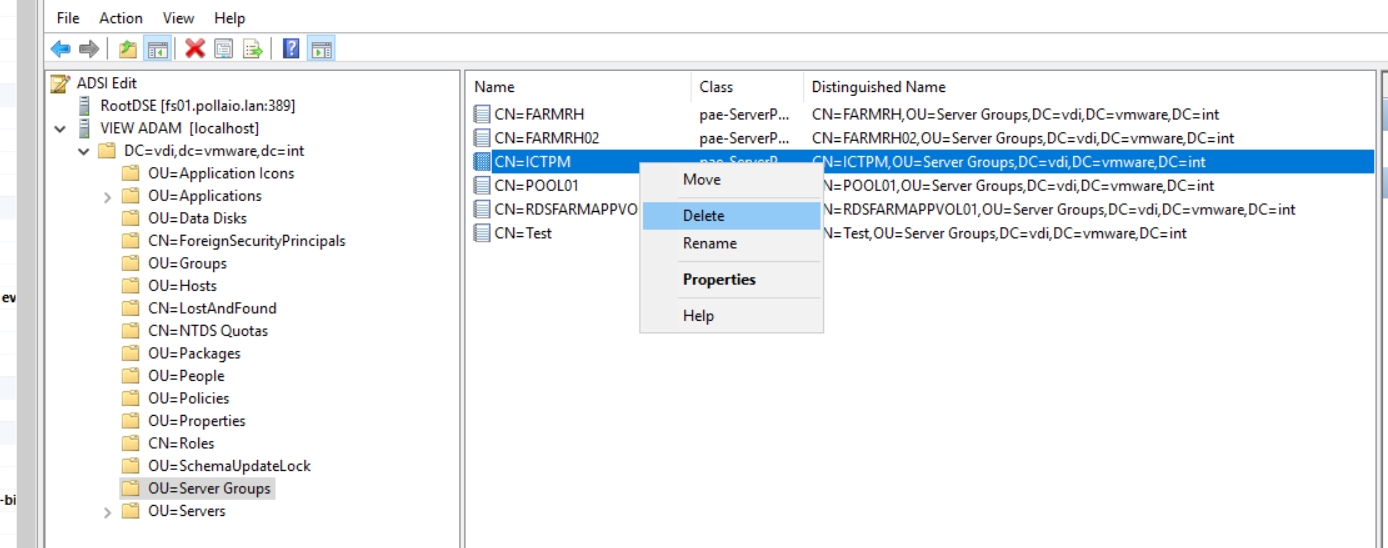
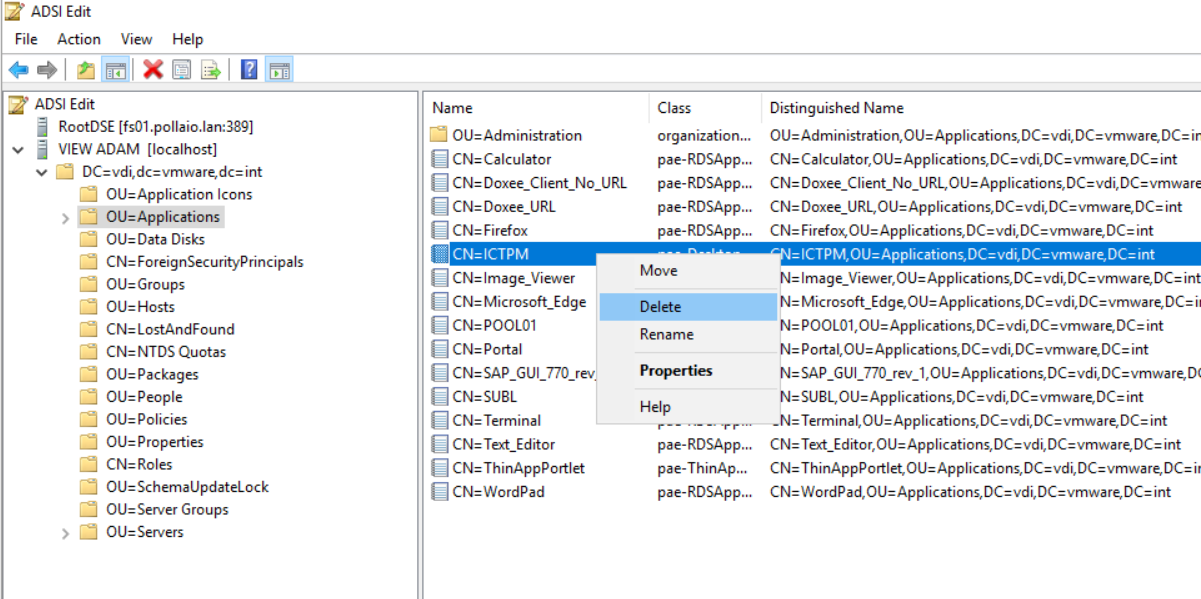
If the Pool in question is still present and in a deleting state, we proceed to access the ADSI Edit console and modify the ADAM DB by deleting the references left to the pool in deleting state (in my case ICTPM)
- Remove Desktop Pool from ADAM Database
To connect follow this KB:
Connecting to the Horizon View Local ADAM Database (vmware.com)
remove the pool from Adam as follows.