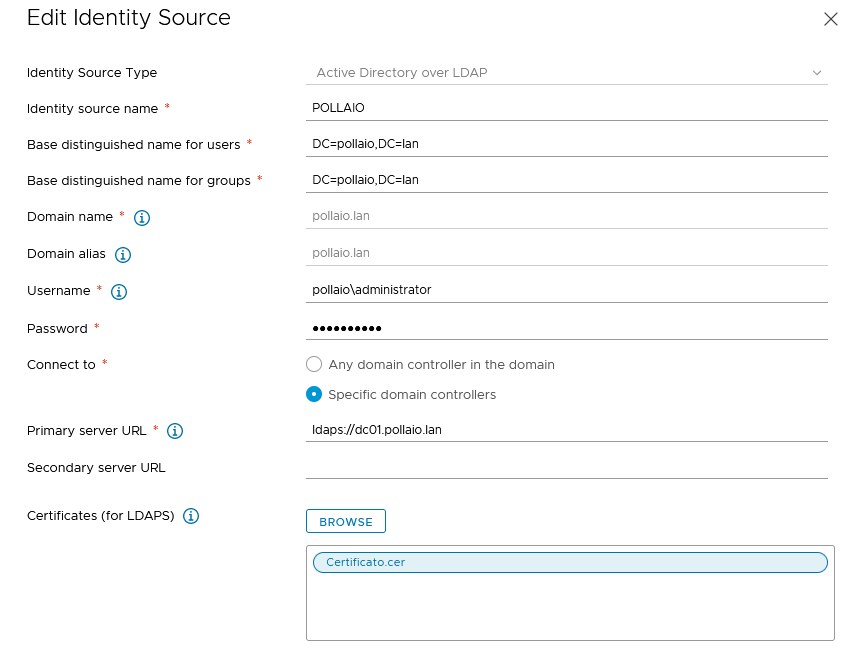
Few people know that it is possible use Linux Distribution to create VDI desktop or Stream Application (Like RDS) to publish it with Horizon.
The desktop pool can to be Instant Clone or Full Clone.
In the last Horizon version (2312) there is a new functionality to configure the agent, the function have to objective to simplify the installation and also configure the OS ((Like the joined to Active Directory domain).
In the Horizon Agent for Linux package there is a new command file:
easyinstall_viewagent.sh
We can use this command for:
- Configure Linux OS template
- Install Horizon Agent
For complete all previous steps you can start this command (with root privileges)
./easyinstall_viewagent.sh
The command do:
Platform check
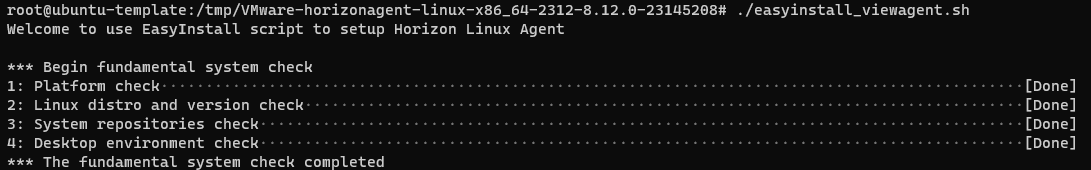
Now you need to insert information like DNS, Hostname, Domain and Account to join to domain
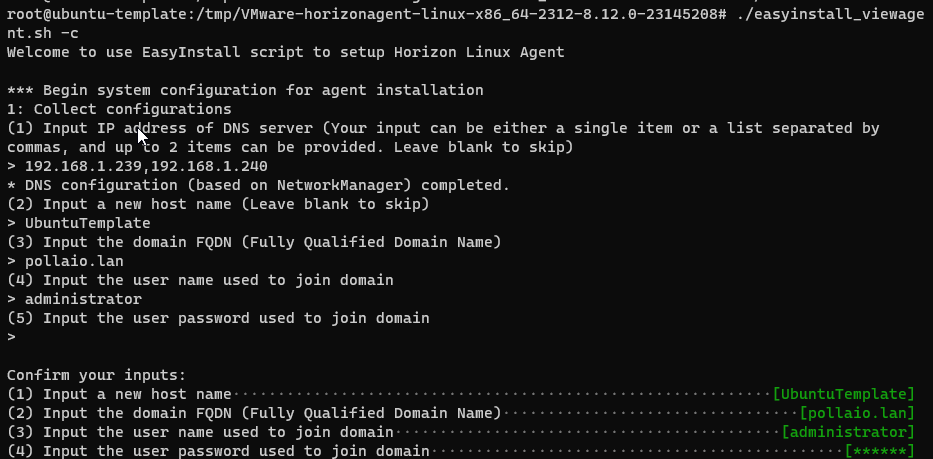
Now the script check and install missed packages (SSSD etc.…) and make the domain join
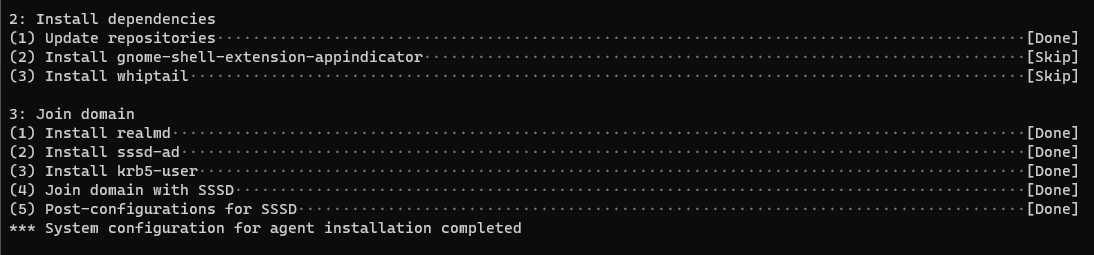
After joined the template to AD domain the script start to install the horizon agent
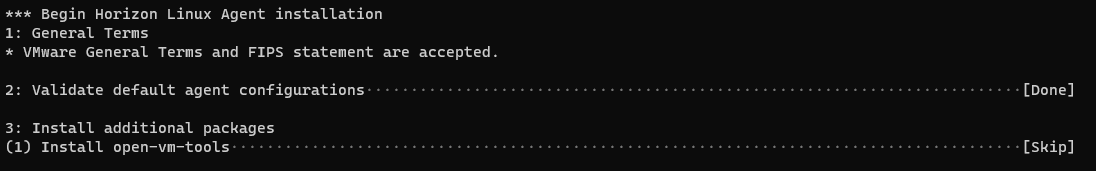
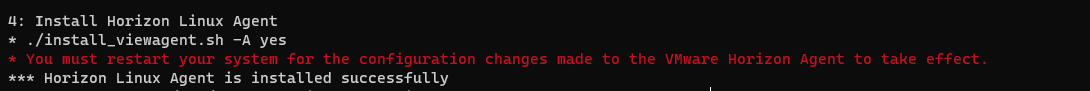
Now the Linux GoldI mage is ready to use for create a Horizon instant clone desktop pool or used for Full Clone Desktop Pool.
It is possible to configure the OS and install Horizon Agent in two different steps
- Configure OS
- For configure user Linux OS use this command:
./easyinstall_viewagent.sh -c
- Install Agent
- After configure the OS we can install the Horizon agent with this command:
./easyinstall_viewagent.sh -i
With this command we can to use some switch value:
Default (Hostname, Domain FQDN, DOMAIN Join User, DOMAIN Join PASSWORD …)
Advanced (The same option of DEFAULT with NTP, HORIZON AGENT FEATURE and other)
Expert (The same option of Advanced with another function)
In this link more information
Use the Easy Setup Tool to Prepare a Linux Machine (vmware.com)