VMware a few days ago released a new Horizon Version.
The new build 2106 (8.3) brings with it some very interesting features from some relating to the security of intellectual property to those related to the Teams collaboration tool, here is a list of those that I consider the most interesting:
- Implementation of GPO for blocking the ability to take screenshots of VDI sessions from Windows and MAC Clients
- Possibility in the instant clone to use the Microsoft Sysprep (this function slows down the deployment of an IC by performing a series of reboots)
- Functionality for applications of run indefinitely
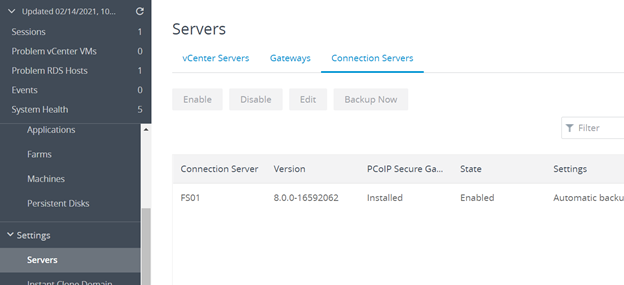
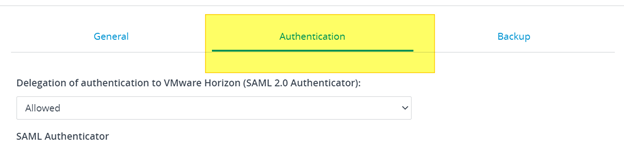
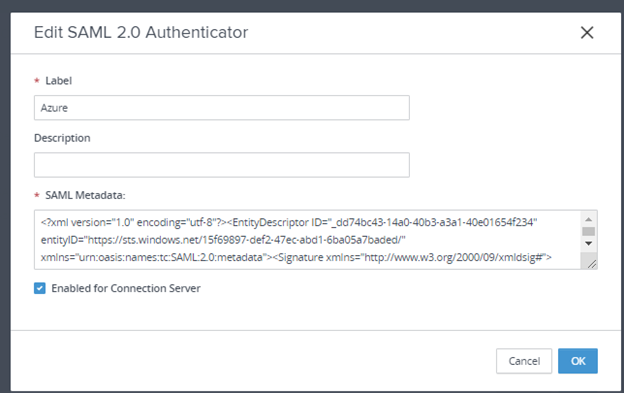
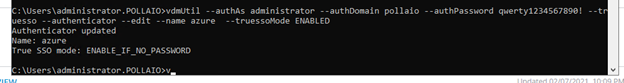
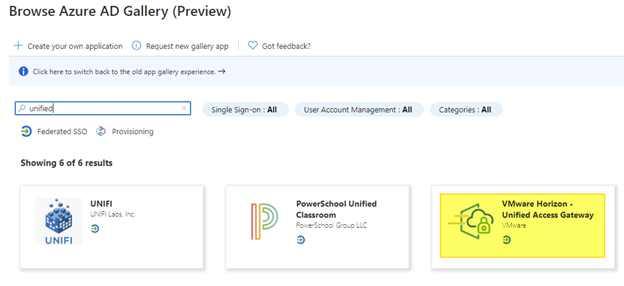
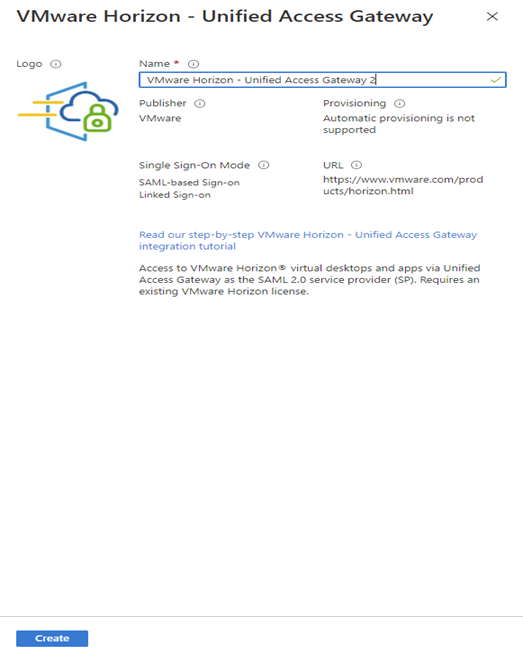
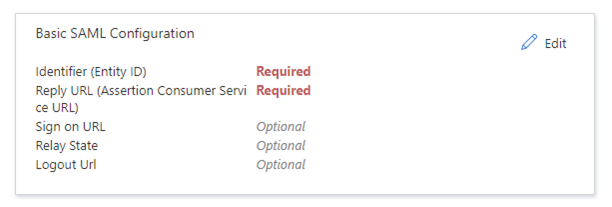
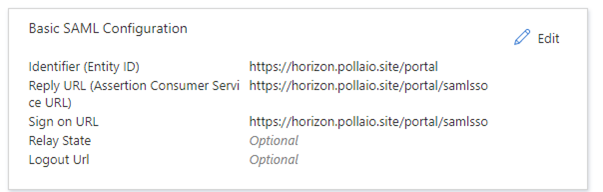
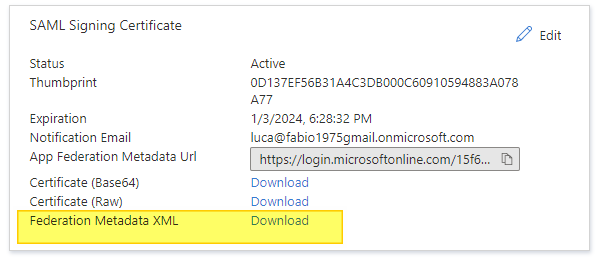
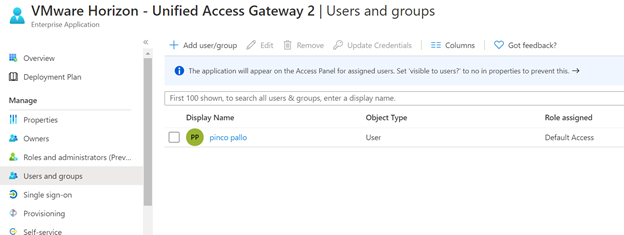
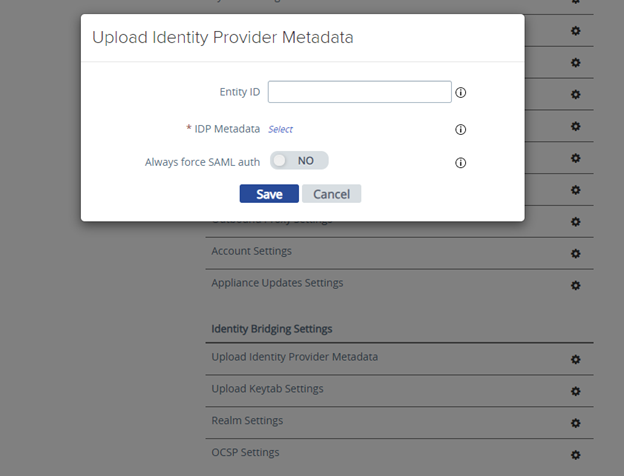
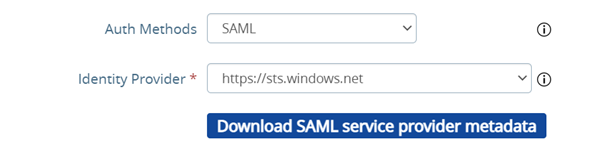
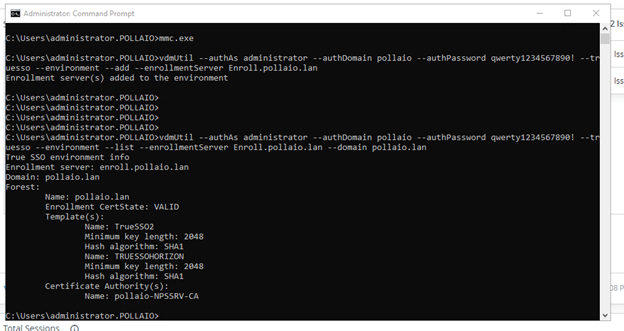
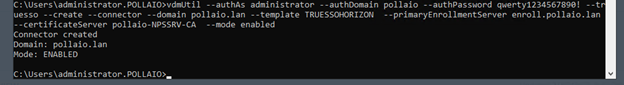
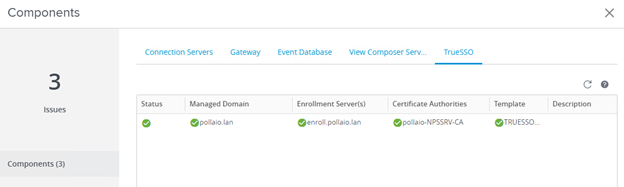
- Possibility to use TrueSSO SAML authentication for non-Trust domains
- Horizon Agent has support for Windows Server 2022 (Currently in Preview)
- The Horizon Client for Linux has the optimization for Teams (as in some versions the functionality for the Windows client was present)
- Cloud Burst support to extend your on-prem workload to the Cloud in case of a high load.
More details in this video