VMware has released the version of Horizon where the LOG4J vulnerability is fixed. (CVE-2021-44228 and CVE-2021-45046)
Build 19067873 is not vulnerable (released 12/16/202), while previous build 19052438 and 18964782 (released 12/14/2021 and 11/30/2021) are vulnerable
CVE-2021-44228
UAG 2111.1
VMware released the UAG (Unified Access Gateway) with a fix for the LOG4J vulnerability
The UAG version is 2111.1
Log4j, Horizon Connection Server Workaround
We continue to look at how to mitigate the log4j vulnerability, in this post we look at horizon connection servers in detail.
As indicated by the VMware KB
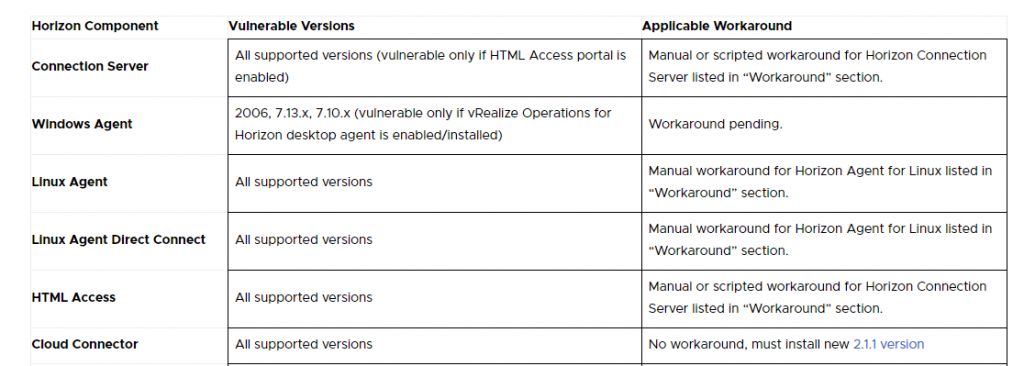
only the connection servers where the HTML Access Portal is active are vulnerable. But all versions are subject to vulnerability.
I recommend applying the workaround even if the HTML Access Portal is not active.
Again as indicated in the previously cited KB we have two possibilities:
- Change the following registry key
1. Edit this registry value:
HKLM\Software\VMware, Inc.\VMware VDM\plugins\wsnm\TomcatService\Params\JVMOptions
2. Append a single space character followed by this text: -Dlog4j2.formatMsgNoLookups=true
3. Exit the registry editor and restart the Connection Server service or reboot the machine
- Run the following script as administrator.
@echo off
setlocal
goto start
__________________________________________________
CVE-2021-44228 - Prevent log4j parameter expansion
Horizon Connection Server 7.x, 8.x
VMware, Inc. 2021
__________________________________________________
:start
set sigpath=HKLM\Software\VMware, Inc.\VMware VDM\plugins\wsnm\TomcatService
for /f "delims=" %%g in ('reg.exe query "%sigpath%" /v Filename') do set sigval=%%g
if "%sigval%"=="" goto notneeded
set killflag=-Dlog4j2.formatMsgNoLookups=true
set svcpath=HKLM\Software\VMware, Inc.\VMware VDM\plugins\wsnm\TomcatService\Params
for /f "tokens=2*" %%v in ('reg.exe query "%svcpath%" /v JVMOptions') do set svcval=%%w
echo %svcval%|find " %killflag%" >nul
if not errorlevel 1 goto notneeded
reg add "%svcpath%" /v JVMOptions /d "%svcval% %killflag%" /f
net stop wsbroker /y && net start wsbroker
echo Completed.
goto :EOF
:notneeded
echo Not required.
goto :EOF
I will proceed with the script.
I create a fix-log4j.bat file in the c: \ temp folder of my connection server and copy the script text to it.
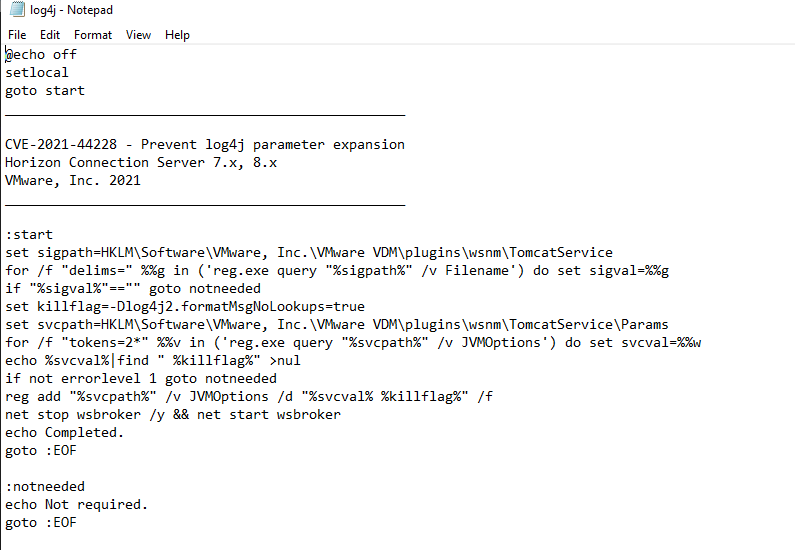
I launch the command from a PowerShell with administrator rights:
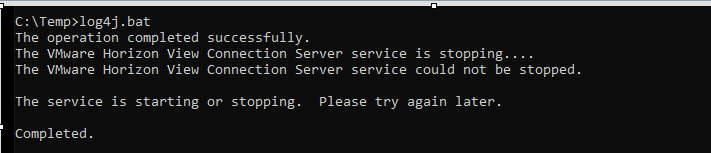
I reboot the server
I verify that the workaround is applied by relaunching the bat file.
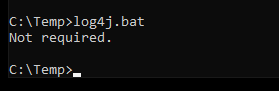
Obviously, I have to do this on all the Horizon Connection Servers present
in the Horizon infrastructure
Automate workaround for mitigating Log4j exploit on VCSA (vCenter Virtual Appliance)
After the post where I apply the VMware workaround for mitigating the Log4j exploit on the UAG appliance, now I suggest using this VMware KB to apply the workaround on vCenter.
The Python script attached at the KB check the vCenter version (6.5, 6.7 and 7) and apply the correct workaround indicate from VMware [see the Workaround instructions to address CVE-2021-44228 in vCenter Server and vCenter Cloud Gateway (87081) (vmware.com)]
VMware, CVE-2021-44228 and log4j (version 2)
Since the end of last week, a new critical vulnerability has spread, present in many programs (Many VMware applications use this Java Logging including vCenter, Horizon, etc.)
“an exploit in the popular Java logging library log4j (version 2) was discovered that results in Remote Code Execution (RCE) by logging a certain string.” as indicated in this link:
https://www.lunasec.io/docs/blog/log4j-zero-day/
After a few hours, the CVE also released its bulletin (CVE-2021-44228).
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2021-44228
On the day of 10/12/2021, VMware released its security advisor (VMSA-2021-0028) with the workarounds to limit the vulnerability pending the release of patched versions to fix it:
https://www.vmware.com/security/advisories/VMSA-2021-0028.html
So good application everyone!

By the way, for the uninitiated:
What is CVE? CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that’s been assigned a CVE ID number.
Security advisories issued by vendors and researchers almost always mention at least one CVE ID. CVEs help IT professionals coordinate their efforts to prioritize and address these vulnerabilities to make computer systems more secure.