## UPDATE 20/12/2021 ##
On December 14, 2021 the Apache Software Foundation notified the community that their initial guidance for CVE-2021-44228 workarounds was not sufficient. We believed the previous instructions in this article to be an effective mitigation for CVE-2021-44228, but in the best interest of our customers, we must assume the earlier workaround may not adequately address all attack vectors.
We need to run a script:
#!/bin/bash
# Log contents to file by prefixing timestamp. Maximum file size is 50MB
function log_to_console() {
echo "$(date +'%Y-%m-%d %T')" "$HOSTNAME" "$@"
}
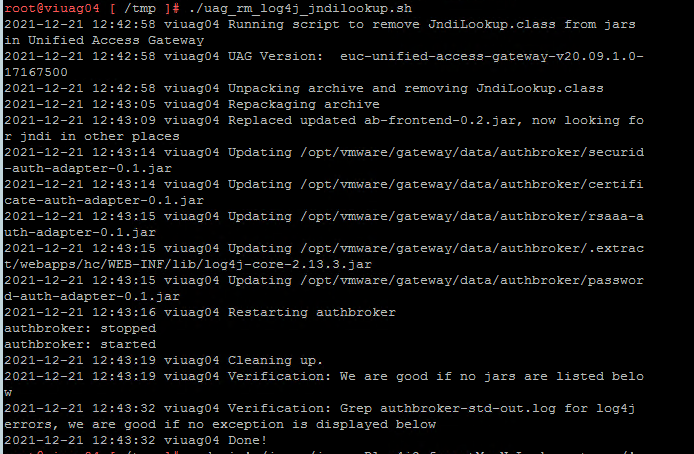
log_to_console "Running script to remove JndiLookup.class from jars in Unified Access Gateway"
log_to_console "UAG Version: " $(tail -1 /opt/vmware/gateway/logs/version.info 2>/dev/null)
mkdir /tmp/test
mkdir /tmp/bkp
log_to_console "Unpacking archive and removing JndiLookup.class"
cp /opt/vmware/gateway/lib/ab-frontend-0.2.jar /tmp/bkp
unzip -q -o /opt/vmware/gateway/lib/ab-frontend-0.2.jar -d /tmp/test
unzip -q -o /tmp/test/hc.war -d /tmp/test/hc
zip -dq /tmp/test/hc/WEB-INF/lib/log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
rm /tmp/test/hc.war
cd /tmp/test/hc
zip -r -q ../hc.war .
cd ..
rm -rf hc
log_to_console "Repackaging archive"
zip -r -q ab-frontend-0.2.jar .
chown gateway:users ab-frontend-0.2.jar
mv ab-frontend-0.2.jar /opt/vmware/gateway/lib
log_to_console "Replaced updated ab-frontend-0.2.jar, now looking for jndi in other places"
find / -type f \( -name "*.jar" -o -name *.war \) -exec sh -c "zipinfo -1 {} 2>/dev/null | grep 'JndiLookup.class' && echo {}" \; | grep .jar | while read -r line ; do
jar_path=$line
log_to_console "Updating $jar_path"
zip -dq $jar_path org/apache/logging/log4j/core/lookup/JndiLookup.class
chown gateway:users $jar_path
done
log_to_console "Restarting authbroker"
supervisorctl restart authbroker
log_to_console "Cleaning up."
cd /tmp
rm -rf /tmp/test
log_to_console "Verification: We are good if no jars are listed below"
find / -type f \( -name "*.jar" -o -name *.war \) -exec sh -c "zipinfo -1 {} 2>/dev/null | grep 'JndiLookup.class' && echo {}" \;
log_to_console "Verification: Grep authbroker-std-out.log for log4j errors, we are good if no exception is displayed below"
cat /opt/vmware/gateway/logs/authbroker-std-out.log | grep log4j
log_to_console "Done!"
Well we need to connect to UAG and create a uag_rm_log4j_jndilookup.sh file
vi uag_rm_log4j_jndilookup.sh
copy into the file the code, and enable it for execution
chmod +x uag_rm_log4j_jndilookup.sh
running the script
./uag_rm_log4j_jndilookup.sh
now if the UAG version is between 2009 and 2111 it is also necessary to set the -Dlog4j2.formatMsgNoLookups=true option on the authbroker service with the following commands. Note the space between “s/java /java” and a space after “true /” in the command, these are important to ensure the command works correctly and doesn’t attempt to modify the wrong lines in the configuration file.
sed -i ‘s/java /java -Dlog4j2.formatMsgNoLookups=true /’ /opt/vmware/gateway/supervisor/conf/authbroker.ini
and restart the supervisorctl
supervisorctl update
more info in this VMware KB
#########################
In the middle of December month, we found a “little exploit”……
Ok it is not a joke, for mitigate on UAG (Unified Access Gateway that is a Security Server exposed on the Internet for remote access at Horizon infrastructure) it is necessary (To apply the workaround for CVE-2021-44228 to Unified Access Gateway version 2009 through to 2111):
- Connect to UAG server with SSH Session
Check if SSH is enabled on UAG server to accept root connection.
Connect from WEB console or VMware Remote Console to UAG virtual appliance and modify in /etc/ssh/sshd_config the following line (for modify use vi commands):
PermitRootLogin no
to
PermitRootLogin yes
Save the file
Restart SSHD service with this command:
service sshd restart
now you are able to create an SSH connection to UAG server, REMEMBER TO DISABLE SSH CONNECTION FOR ROOT USER WITH ROLLBACK THE SETTING INTO SSHD_CONFIG FILE
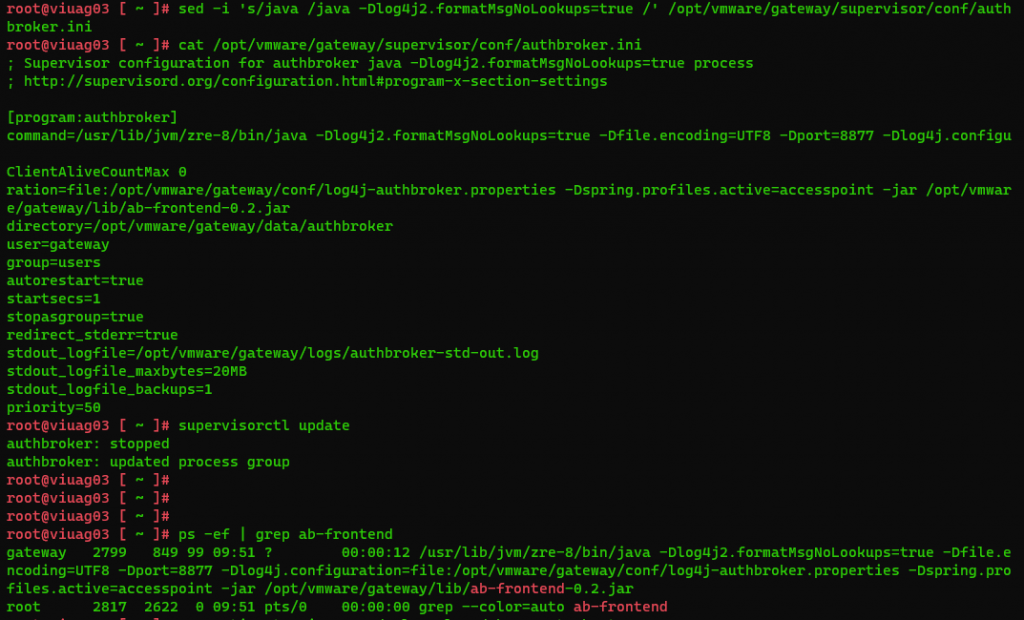
- Append the fix -Dlog4j2.formatMsgNoLookups=true
Type this command:
sed -i ‘s/java /java -Dlog4j2.formatMsgNoLookups=true /’ /opt/vmware/gateway/supervisor/conf/authbroker.ini
Reload the service
supervisorctl update
Check if the fix is applied with this command:
ps -ef | grep ab-frontend
the output of the command should need:
root@viuag03 [ ~ ]# ps -ef | grep ab-frontend
gateway 2799 849 99 09:51 ? 00:00:12 /usr/lib/jvm/zre-8/bin/java -Dlog4j2.formatMsgNoLookups=true -Dfile.encoding=UTF8 -Dport=8877 -Dlog4j.configuration=file:/opt/vmware/gateway/conf/log4j-authbroker.properties -Dspring.profiles.active=accesspoint -jar /opt/vmware/gateway/lib/ab-frontend-0.2.jar
root 2817 2622 0 09:51 pts/0 00:00:00 grep –color=auto ab-frontend
Ref: Workaround instructions to address CVE-2021-44228 in VMware Unified Access Gateway (87092)